Cloud Foundry Advisory Board Meeting, Sep 2020: Quarks Updates

This month’s Cloud Foundry Community Advisory Board (CAB) meeting featured two community presentations: templated configs (a new feature in Project Quarks) and automated patching of application images in Cloud Foundry for Kubernetes. The call attendees also discussed regular development updates around the ecosystem projects and the upcoming European summit. The call was moderated by Troy Topnik from SUSE.
Templated configs in QuarksSecret
While Kubernetes is the gold standard for automating deployment, scaling, and managing containers, it does not have a unified model for cloud-native application delivery. Project Quarks aims to resolve this issue by providing Kubernetes users with the benefits of the Cloud Foundry Application Runtime (CFAR), including an end-to-end application life cycle management platform and a consistent developer experience.
Quarks integrates Cloud Foundry and Kubernetes by packaging the CFAR as containers rather than virtual machines. Specifically, the project uses BOSH releases to create Docker images. Once the images are deployed into Kubernetes, operators no longer need to rely on BOSH to manage the CFAR. This way, Quarks is able to provide an operator experience that is familiar for Kubernetes users.
Quarks is made up of several components, one of which is QuarksSecret. This component is responsible for generating secrets inside a Kubernetes cluster.
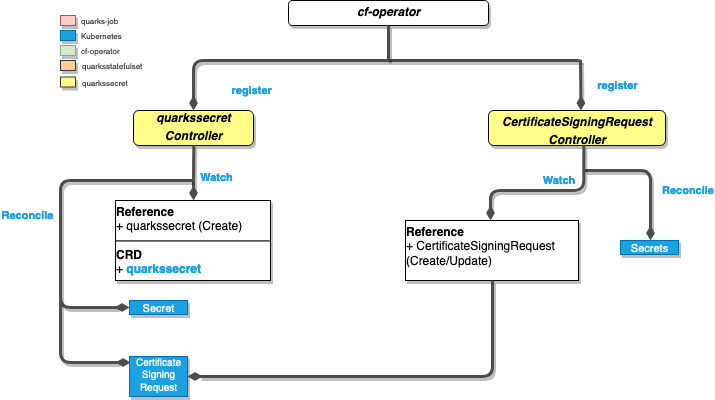 QuarksSecret and the associated set of controllers (Image credit)
QuarksSecret and the associated set of controllers (Image credit)Mario Manno of SUSE demonstrated a new feature of QuarksSecret—templated configs—designed to enable KubeCF to consume the new Kubernetes release of User Account and Authentication. This will allow users to fill out a template with values from existing secrets and output the result to another secret. For more details about QuarksSecret, check out the project’s documentation or Pivotal Tracker.
 Templated configs demo (Image credit)
Templated configs demo (Image credit)
Automated patching of app images in cf-for-k8s
In the BOSH-based world of Cloud Foundry, according to Paul Warren of VMware, application stack updates are provided to the platform via Cloud Foundry Linux BOSH releases. Diego then uses the base file systems to patch all of the pushed apps simultaneously.
“Kubernetes does not have BOSH and, therefore, does not have an equivalent to Cloud Foundry BOSH releases. So, how will applications stack updates happen?”
—Paul Warren, VMware
To remedy the problem, the CAPI team has been working on automated patching of application images in Cloud Foundry for Kubernetes.
During the call, Piyali Banerjee of VMware demoed the team’s work. She also noted a couple of features under development. The first one will help operators to understand how the stack update is progressing. The second will provide application rollbacks without requiring developers to repush and restage.
 A stack update demonstration (Image credit)
A stack update demonstration (Image credit)Cloud Foundry for Kubernetes’s GitHub repo
Runtime PMC
Eric Malm of VMware reported the following development highlights:
- The CLI team released CLI v6.52.0 and v7.1.0. The updates include commands for rollbacks and revisions.
- The Release Integration team delivered Cloud Foundry for Kubernetes v0.6.0 with application base-image updates. They are working on uniform configuration interface.
- The KubeCF team released v2.4.0 with multistack support. The team is working on resource limits and request configuration for system components.
- The CAPI team is moving application packages out of the blobstore and into the Open Container Initiative image registry in Cloud Foundry for Kubernetes.
- The Eirini team has completed with application tasks and
CF_INSTANCE_INDEXsupport. They are making progress on custom resource definitions. - The Networking team is continuing to work on scalability and also exploring the pluggability of other Ingress systems.
- The Logging and Metrics team is improving the performance and scalability of Log Cache.
BOSH
Kevin Rutten of Stark & Wayne noted that there was a Common Vulnerabilities and Exposures high-risk alert on the Linux kernel. Users should bump up to the latest stemcell. He added that the BOSH team is preparing some more additional releases soon.
BOSH’s GitHub repo | BOSH’s Pivotal Tracker
Stratos
Troy Topnik from SUSE mentioned the release of Stratos v4.1 and v4.2. He explained that SUSE has been maintaining extensions for Kubernetes in the downstream of Stratos. Troy announced that the company will be donating v4.1 and v4.2 to the Foundation. This will help to expose a number of Kubernetes features for users to try out.
CF Extensions’ GitHub repo | Stratos’s GitHub repo
Foundation updates
Chip Childers of the Cloud Foundry Foundation announced that the European summit is scheduled for October 21–22. Similar to the North American summit earlier this year, it will be held virtually. He emphasized that the theme for the conference will be collaboration, and many of the presentations will focus on this subject. Community award nominations are still open.
Chip also implored the members of the Cloud Foundry community to assist in surveying end users and gather information as to how they make use of the technology. Data gathered from the survey will help to steer the direction of Cloud Foundry’s development. Specific individual and company information will not be shared.
Chris Clark posted a biweekly technical round-up where you can learn about prominent releases, some other updates and news, as well as community events for September.
The next CAB call is tentatively scheduled for October 21, 2020, at 8 a.m. PDT. Anyone interested can join Cloud Foundry’s CAB Slack channels.
















