Cloud Foundry Advisory Board Meeting, Jan 2021: New Roles and cf-for-k8s

This month’s Cloud Foundry Community Advisory Board (CAB) meeting featured discussions around the future of сf-for-k8s. A proposal for two new Cloud Foundry roles was also brought up. The teams provided development updates around the ecosystem projects as usual. The call was moderated by Troy Topnik from SUSE.
cf-for-k8s: Use cases and incompatibilities
cf-for-k8s combines prominent Cloud Foundry developer APIs with Kubernetes, Istio, and other open-source technologies. The project aims to improve developer experience for organizations running Kubernetes.
Bernd Krannich of SAP shared a couple of documents that discuss possible use cases for cf-for-k8s in the future, as well as known incompatibilities with cf-deployment and KubeCF. Among other things, the documents break down a few scenarios that should be possible with the continued improvement of cf-for-k8s:
- separating the Cloud Foundry control plane from the apps
- having multiple Kubernetes clusters running Cloud Foundry apps
- running multiple control planes on Kubernetes clusters
- hibernating the control plane
- changing the control plane persistency from Postgres to etcd
“At SAP, we expect to run into quite a few cf-for-k8s deployments, which over time, people who are running Cloud Foundry on virtual machines will move toward to. Once we have feature parity, these new deployments can be good evolutionary steps to make it easier for us to operate and manage multiple environments. The primary idea here is different from what we have today, which is running the Cloud Foundry control plane and apps in the same Kubernetes cluster. The idea is separating those into different clusters.” —Bernd Krannich, SAP
The documents are still works in progress, and Bernd is looking for feedback from the community.
New roles for Cloud Foundry
Stephan Klevenz of SAP shared a proposal to create two new roles in Cloud Foundry to add fine-granular controls. According to Stephan, the proposal aims to fix two common problems shared by multiple Cloud Foundry users. First, it is easy to delete data by accident. These accidents take a lot of effort to fix and are very costly. Second, organizations running Cloud Foundry all have different models that dictate how they operate and run apps. The lack of a fine-grained control on authorizations leads to leakage of credentials and unauthorized access to sensitive data.
The two new proposed roles are a space application developer and a space operator.
A space application developer will be able to perform all necessary operations on an app, as well as read, bind, and unbind service instances. Under this role, it will be impossible to create, update, or delete service instances.
A space operator will be able to start, stop, and restart apps, as well as view life cycle events for an app and display action logs. Furthermore, the role is entitled to scaling apps, but restricted from displaying an application environment. In terms of working with service instances, the role will have the very same permissions as a space application developer.
“We need a powerful and flexible permission model. This was the goal with the CF Permissions project, but that ended in June. A minimal change to address customer concerns are to introduce two new roles to the Cloud Controller.” —Stephan Klevenz, SAP
Runtime PMC
Eric Malm from VMware noted the following updates:
- The Release Integration team delivered cf-deployment v15.6.0 and is soon to push cf-for-k8s v2.0.0 live.
- The KubeCF team is bumping dependencies and is working toward KubeCF v2.8.0.
- The CAPI and Services API teams are continuing to close out the endpoints for Cloud Controller API v3.
- The Eirini team is considering restoring its staging tasks due to incompatibility issues with Paketo Buildpacks and other Cloud Foundry buildpacks. They are also exploring component observability.
- The Diego team bumped to Golang v1.15. They also tweaked the HTTP encoding of the bulletin board system event stream to accommodate Golang v1.15 clients.
What’s next?
Chris Clark from the Cloud Foundry Foundation highlighted that the switch to the new contributor license agreements was smooth. Anyone with issues should reach out to Chris.
Recently, the foundation published Cloud Foundry User Survey 2020. The key findings reflect on how the PaaS helps to reduce the development cycle and support mission-critical software, as well as contemplates the joint usage of the platform with Kubernetes.
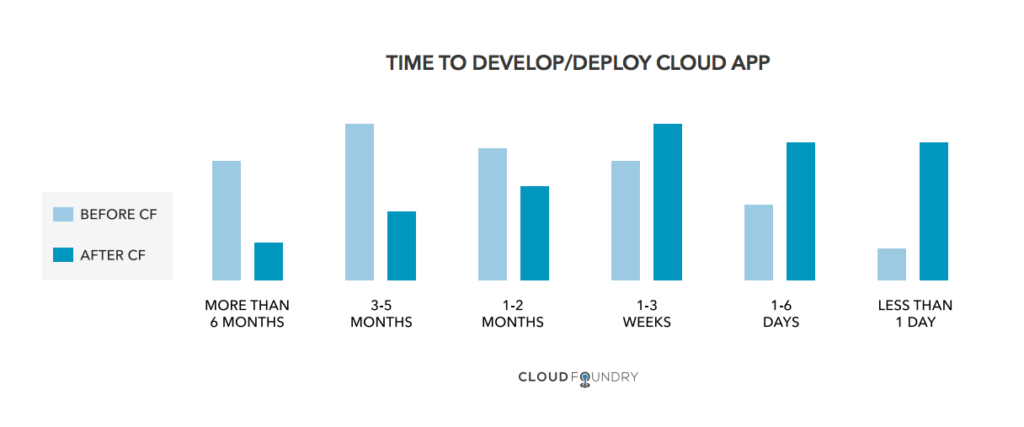 Findings from Cloud Foundry User Survey 2020 (Image credit)
Findings from Cloud Foundry User Survey 2020 (Image credit)In his latest biweekly technical round-up, Chris noted the release of Stratos v4.4.0 and Routing-release v0.211.0.
Similar to 2020, the Foundation has no plans to hold in-person events this year. Dates for upcoming summits will be announced in a month. In the next few days, you cn attend a handful of events, including CF Technical Governance meeting (January 22), CF Extensions PMC meeting (January 25), and “cf-push for Modern Observability” webinar with DataDog (January 26).
The next CAB call is tentatively scheduled on February 17, 2021, at 8 a.m. PDT. Anyone interested can join Cloud Foundry’s CAB or cf-operators Slack channels.













