Applying Data-Centric Approach to Unify IoT Security Policies
More data, more challenges
The Internet of Things (IoT) is driving significant new IP traffic, creating more complex security challenges for enterprise IT. Projections from one major technology company show steady 20 to 25% data growth over the next few years, resulting in a doubling every three years or so. Add to this related growth of IoT devices—more devices means more threats—and consequent security challenges for IoT data.
At the recent meetup, Prasad Mujumdar, an engineer with BlueTalon, focused on how “a data-centric security approach can unify all security policies around data for full visibility and better control.”
“How do I make sure the right people are allowed to see [the data], and those who are not are not allowed to access it no matter what apps they are trying to use?” —Prasad Mujumdar, BlueTalon
Prasad mentioned the issue of being able to move data from one app to another while retaining secure compliance. “If you have a file system on a NoSQL database, and move it to Hadoop or another database (of any type), or to a data science application, (in all cases) you need to have a consistent security policy across the pipeline,” he said. “It doesn’t matter what you’re running, you should see the exact same ID and rules enforcement attached to that data.”
Regulations and security policy requirements
Prasad introduced some of the regulatory trends and “scary stories” for companies that fail to be in compliance. The violation of officially established regulations may result in huge fines.
For example, Facebook is daily facing fines of €250,000 in Belgium as European Court of Justice has declared Safe Harbor invalid, which means that tracking data from non-members is illegal. Similarly, the data breach experience of Target—a large discount store retailer in US—resulted in a 46% drop in profits in 2013 due to reputational damage (with additional $100 millions to upgrade the affected systems).
Prasad then outlined a few business-level policy issues for enterprises to keep in mind as they grapple with security issues:
- Data owners and regulatory entities define policies of use.
- Definition of policies must be owned by business stakeholders.
- Automated enforcement of policies across data platforms is needed.
- Policies managed by business owners must be enforceable independent of data platform.
- Enforcement of these policies must be demonstrable to auditors.
- Enforcement must be distributed and consistent.
How this relates to IoT
Prasad noted that in addition to many users, an IoT deployment will have many, that is, heterogeneous data flows. “The biggest problem with these data flows is getting a consistent policy,” he said. The policy extends beyond basic rules, according to Prasad.
Thus, behavior must also be taken into account. For example, “you should know who’s doing what in your system. Who’s running too many reports, for example? You must be able to stop them, or alert someone there might be a hack in your system.”
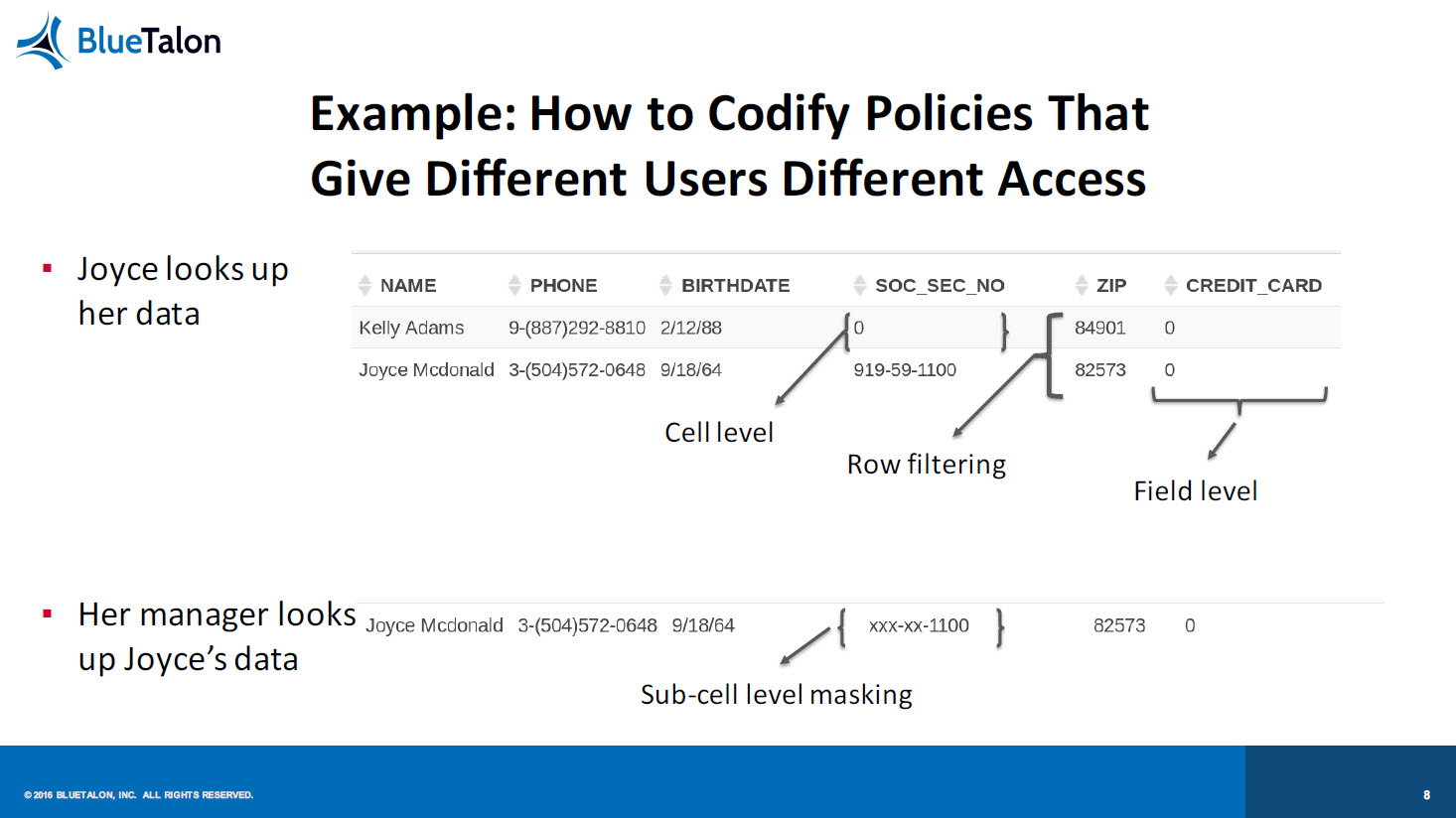
Prasad then focused on how to codify policies that give different users different access:
Addressing the problem
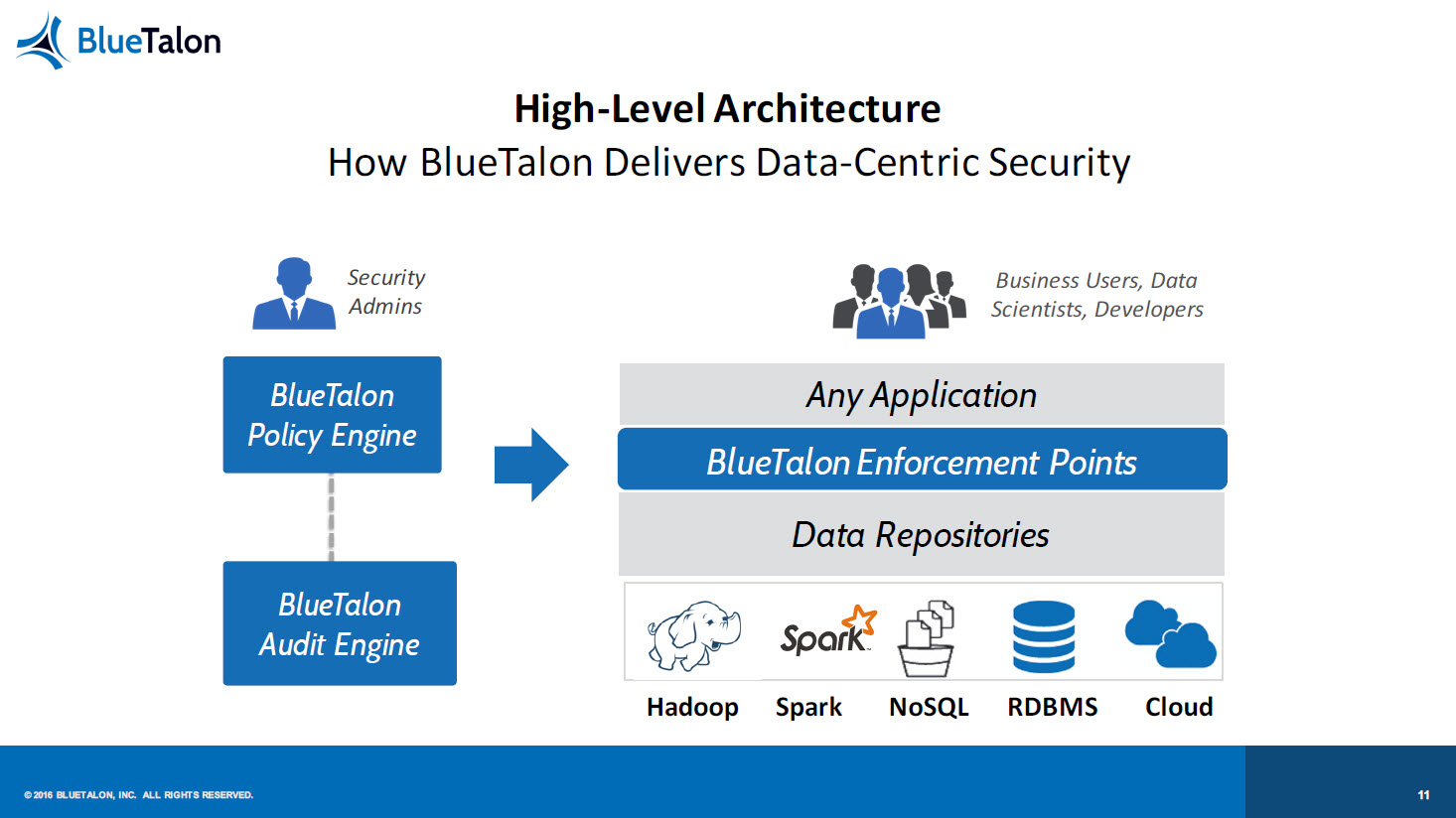
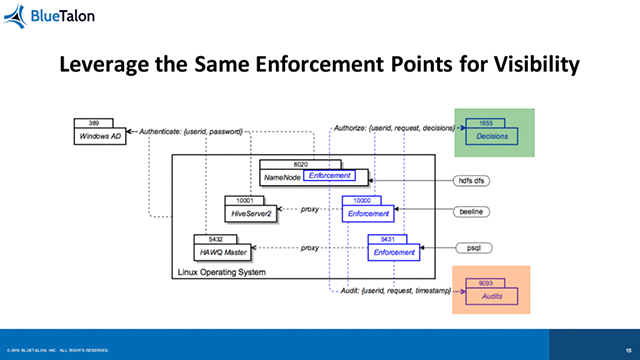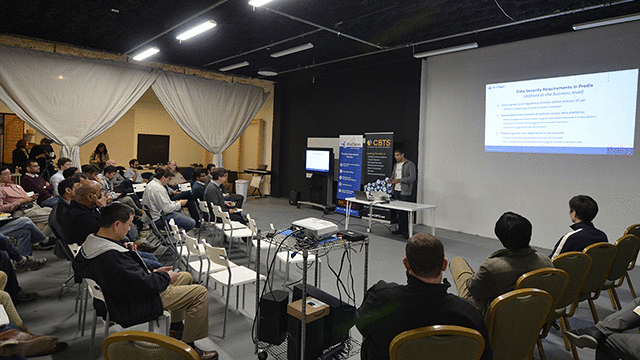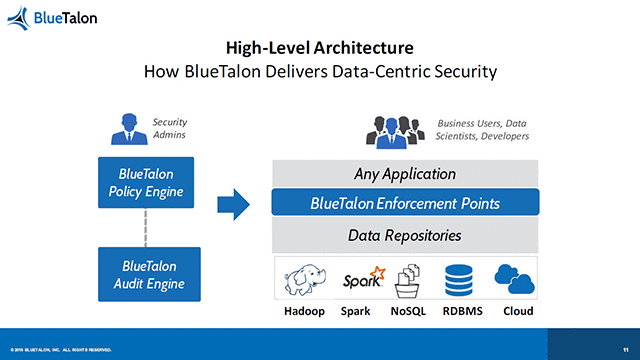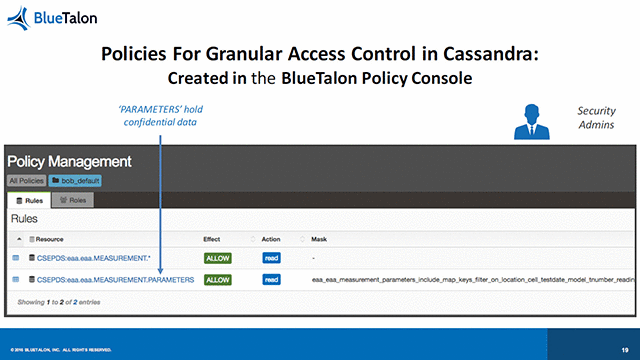
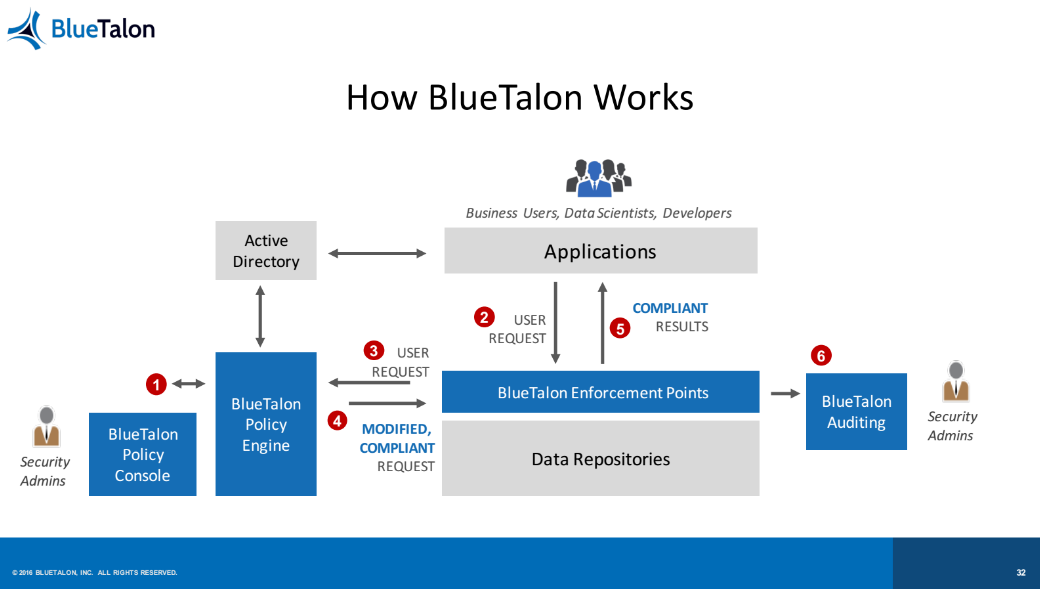
“Don’t change tools just because you put up a security layer,” Prasad exhorted. He described how BlueTalon—a platform for defining fine-grained data access policies applied to all users, all applications, and multiple data stores—was developed to address these issues.
Prasad emphasized the importance of centralizing decisions to manage policies from one place, as well as making the enforcement protocol transparent “to preserve the UX,” reiterating the commitment to the user experience he mentioned earlier in his talk.
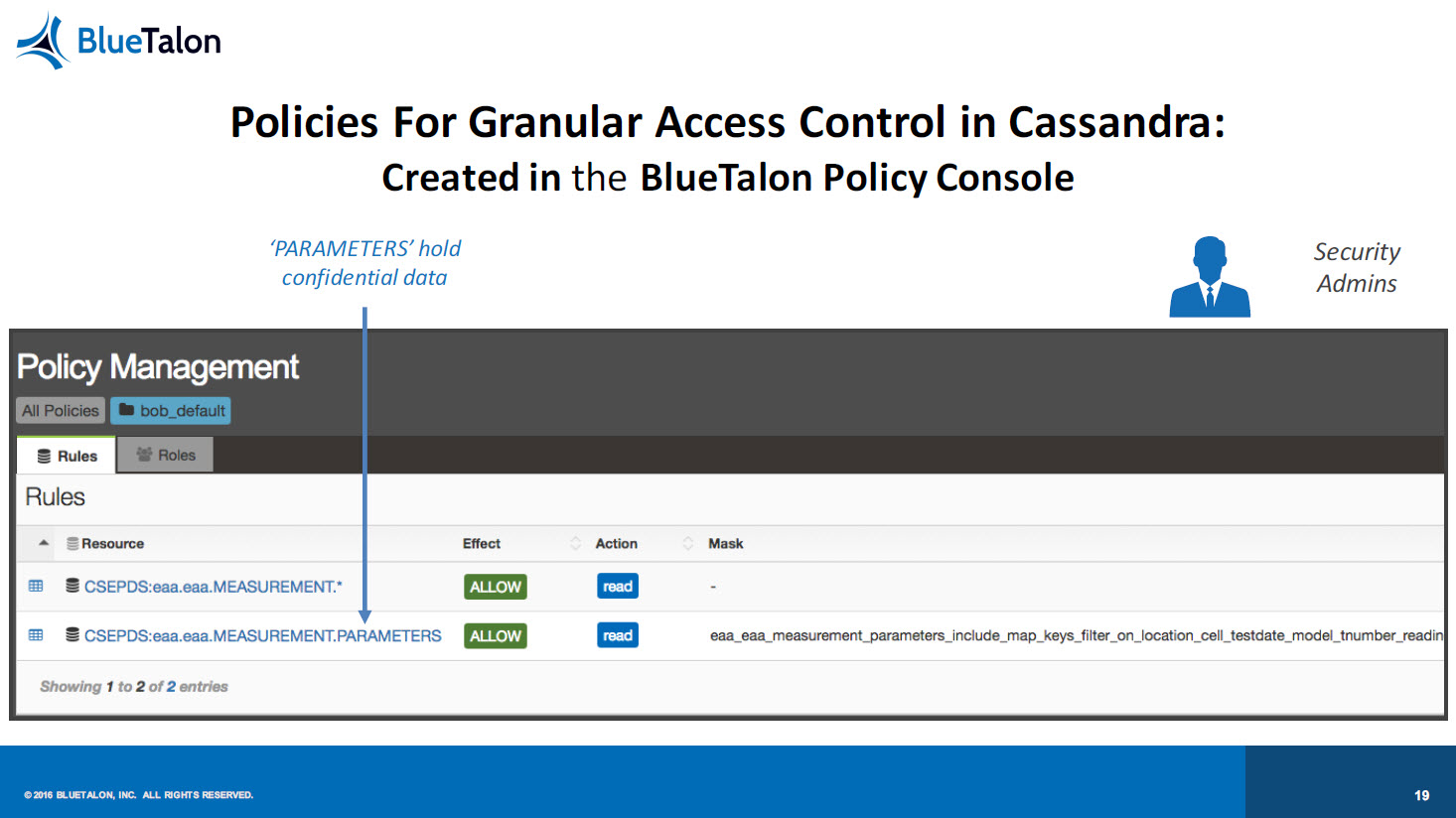
An example using Cassandra
The Cassandra NoSQL database is one of the options available for use with the Predix platform, and Prasad provided some examples of the issues that arise with its use. For example, one security feature is limited to a simple Grant/Revoke command at the table level, giving it an “all or nothing” approach to access. Each user must be recreated on every local Cassandra node for authentication.
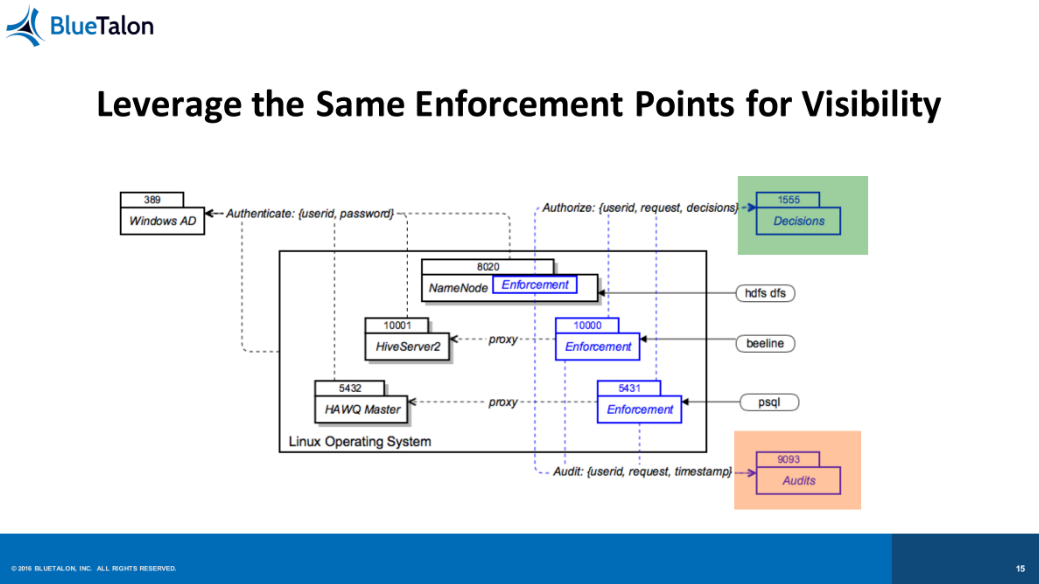
In contrast, implementing BlueTalon provides “granular, user-based access controls to columns and sub-fields,” Prasad said. Dynamic attribute resolution and proxy authentication is enabled, and it’s possible to conduct auditing of user data requests to monitor compliance or check on anomalous behaviors. He also noted a very minimal performance impact through BlueTalon’s use, saying that users will be unaware of its existence.
In conclusion, he said the company’s approach “unifies security in the data platforms embedded in Predix,” something that he believes IoT deployers will welcome in coming years as the Internet of Things plays a larger role in their enterprise and drives all those bytes of new data.
For more details on unifying IoT security policies, check out a webinar by Pratik Verma, BlueTalon’s CEO, or watch the following recording from the meetup.
Want details? Watch the video!
Table of contents
|
Related slides
Related reading
- The Good, the Bad, and the Ugly Use of IoT: Who Owns the Data?
- Cybersecurity for the IoT: Issues, Challenges, and Solutions
- Adopting an IoT Platform: Things to Know and Pitfalls to Avoid
- Cloud Foundry and IoT: The Need for Standardization and Transaction Authentication