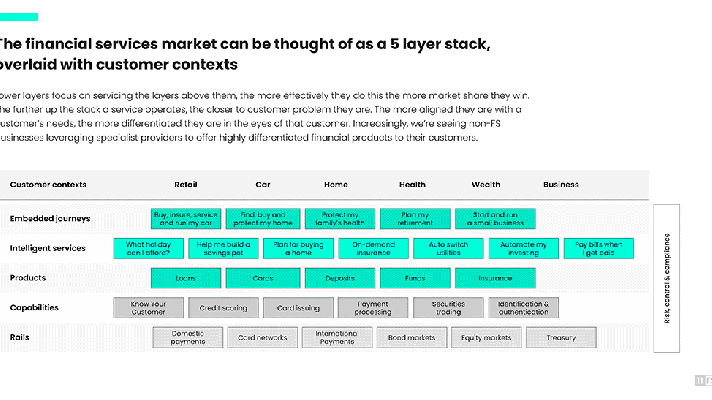
The Technical Aspects of Integrating Know Your Customer Platforms
Onboarding takes too long
Money laundering is the process of disguising financial assets gained from illegal activities, so they can be used as though originating from a legitimate source. It is one of the oldest financial crimes practiced throughout history. In the book, “Lords of the Rim,” author and historian Sterling Seagrave describes how merchants in China hid their wealth to avoid rulers from taxing profits they had gained through trade over 3,000 years ago.
Due to the illicit nature of money laundering, it is impossible to get a precise value on how much money is laundered at any given time. The United Nations Office on Drugs and Crime estimates that the amount of money laundered each year is 2–5% of the global GDP, or $800 billion to $2 trillion.
To prevent financial crime or any other illicit activities, banks, insurers, and other financial institutions have several security measures in place. One of which is Know Your Customer (KYC), the process used by financial organizations to verify customer’s identity/transactions and assess the level of risk an entity poses.
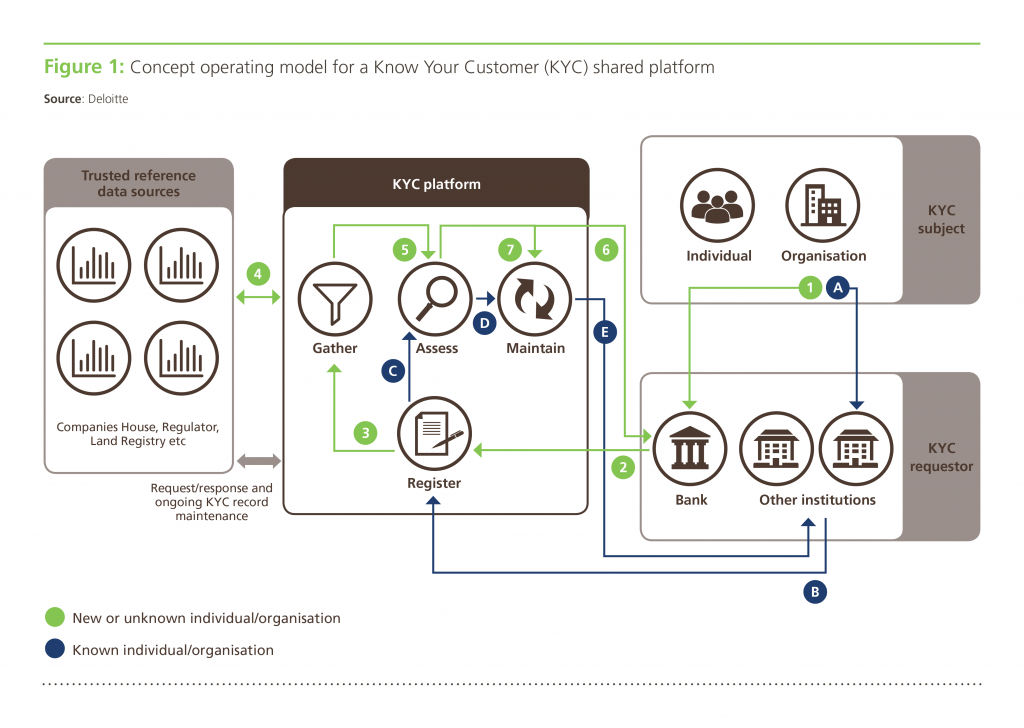 A shared KYC platform workflow (Image credit)
A shared KYC platform workflow (Image credit)However, traditional onboarding of new clients, especially in corporations, involves plenty of manual processes making it both time-consuming and resource-intensive. For instance, to onboard a new client, there are many steps, including, but not limited to the following:
- Gather data. The first step is collecting personal information and data about an individual. This involves manual input of data and the uploading of files such as IDs, proof of residence, credit card information, etc.
- Check documents. Data is extracted from the uploaded files and checked against the information entered manually. Additional checks, such as identity verification through video identification, may be included in this step.
- Verify information. The next step involves screening the person against politically exposed persons (PEP) lists, anti-money laundering (AML) lists, terrorist funding lists, and any other mandatory regulated lists.
- Data remediation. This is an ongoing procedure throughout the KYC process, where outdated information is updated. It typically occurs during specific events, such as an address and name change, or on period reviews.
- Approval. After all the customer information is recorded, the final step is approving or rejecting an application based on all the checks involved.
According to Global Legal Entity Identifier Foundation (GLEIF), onboarding new clientele usually takes six weeks. Due to the length of the process and the possibility of delays, new customers may get frustrated and abandon the account creation process. A report by Signicat, a provider of digital identity solutions, found that 40% of banking customers in the UK renounced their applications. Among those who quit the process, 39% had a problem with onboarding taking too much time.
To speed up the process of onboarding, many third-party service providers offer tools that automate much of the KYC process. With automation, financial institutions can reduce manual workloads by 90% and increase conversion rates twofold. However, the integration of such tools, platforms, and suites may have intricacies of its own.
Popular KYC providers
As financial institutions typically do not have the necessary resources and expertise to automate their KYC processes, many are relying on KYC providers. The following are some examples of KYC service providers around the world.

Alloy was founded in 2015 with a goal to connect banks and fintech companies to more sources of KYC, AML, and other compliance data. The company assists financial institutions to expand their digital product offerings. Alloy also provides services that help to verify applicants who might not have traditional identification, such as a driver’s license.

AU10TIX is an identity management company based in Israel. The company provides critical, modular solutions to link physical and digital identities, so that companies and their customers can confidently connect. AU10TIX’s proprietary technology provides results in less than 8 seconds, allowing companies to onboard faster, prevent fraud, meet compliance mandates, and establish trust with their customers.

Fourthline provides a bank-grade identity stack and expert guidance. The company builds innovative solutions that leverage AI to enable customers to be compliant with ease. Fourthline’s AI-drive platform authenticates millions of identities for top banks and fintechs at a 99.98% accuracy rate.

iComply is a regulatory technology company focused on making financial markets more robust, secure, and efficient. The company provides turnkey compliance automation by simplifying multijurisdictional requirements for nonface-to-face transactions. iComply offers intelligent compliance management solutions in the form of institutional-grade identification and risk mitigation tools that support AML compliance for the entire customer life cycle.

Jumio is a USA-based online mobile payments and identity verification company. Founded in 2010, the company provides card and ID scanning and validation products for mobile and web transactions. Jumio helps organizations to meet regulatory compliance and has verified over 225 million identities issued by 200+ countries and territories from real-time web and mobile transactions.

LexisNexis Risk Solutions provides essential information to aid customers across industry and government to assess, predict, and manage risk. The company’s financial crime screening, payment services, and benefits compliance solutions enable financial inclusion while identifying criminal activity and fraud.

Onfido was founded in 2012 by Oxford alumni. The company uses world-leading artificial intelligence (AI) to assist over 800 companies all over the world in verifying their users. The company’s solutions include document verification, biometric verification, and facial authentication.

Sumsub is an identity verification service company. Founded in 2015, the company provides an all-in-one technical and legal toolkit to cover KYC/AML needs. Trusted by over 1,000 businesses, Sumsub streamlines verification processes with global coverage, generating high approval rates even in emerging and unbanked jurisdictions within South Asia, CIS, LATAM, and Africa.

Thales is a French company that designs and builds electrical systems. In 2019, Thales acquired international security company Gemalto and combined its portfolio with existing digital assets, creating a new leader in digital security. Over 30,000 organizations rely on Thales solutions to verify people.

Trulioo is a Canadian-based provider of electronic identity and address verification for both individuals and businesses. Founded in 2011, the company has an identity marketplace of over 400 trusted data sources.
KYC integration challenges
In a previous blog post, we covered the technical challenges when integrating banking as a service (BaaS). While there are common issues associated with incorporating BaaS and KYC (especially in security and privacy), there are still problems specific to the latter.
Platform API updates are crucial to enforcing security, as well as ensuring all the functionality of a KYC solution works as intended and is available to an organization. Once a KYC provider rolls out the updates, timely changes are required from the customer’s side to safeguard uninterrupted communication between the platform and corporate systems, as well as to prevent technical debt.
Security across all levels—networking, application, and data—is essential to preventing any sort of attack. In addition, integrating a KYC solution via APIs increases vulnerability due to the endpoints that can serve as targets for malicious activity.
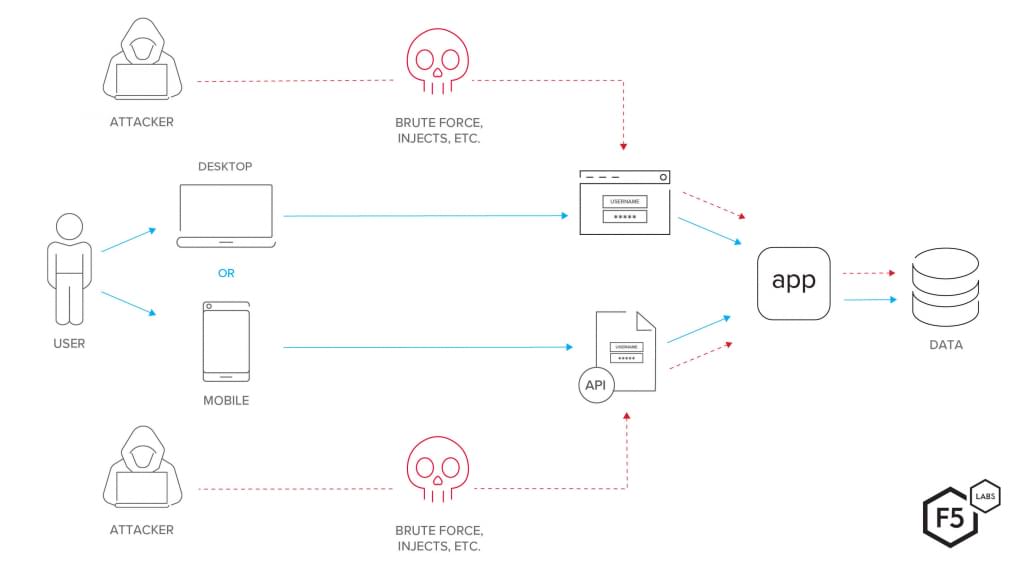 An example of exposed API points (Image credit)
An example of exposed API points (Image credit)Legacy systems built upon an outdated stack may be incompatible with a KYC platform, disrupting integration. Typically, legacy systems represent a monolith, which is difficult to maintain and customize to the needs of integration with a modern KYC platform.
Ongoing monitoring of transactions is crucial to enabling anti-money laundering. Under the Financial Crimes Enforcement Network (FinCEN) Customer Due Diligence (CDD) rule and the Fifth Anti-Money Laundering Directive (5AMLD), financial institutions are expected to create auditable processes for managing ongoing checks. With regulations getting stricter, financial institutions are shifting from traditional periodic customer risk reviews toward real-time transaction monitoring.
Performance may suffer as the integration will inevitably increase the number of POST/GET requests, congesting the network, overloading the queue of events, and prolonging response times of customer-facing apps and core banking systems.
Data quality is something to take care of prior to an integration, as simply buying a KYC platform is not enough. Data degeneration over time and human error during manual updates favor outdated information and duplicates, leaving the KYC platform to run verification against inherently erroneous data. As Bloor Research report states, data degrades very quickly. For example, 7.57% of customers change their jobs in three months and may become unreachable, since their personal corporate contact details is no longer valid. Such data gaps may cost organizations an average of $12.9 million annually, according to a Gartner study.
Mitigating the challenges
Ensure smooth updates
When choosing a KYC platform provider, it makes sense to settle with the one who offers 24/7 support, ready to resolve the issues as they occur, and has a clear roadmap for updates. To minimize the impact on day-to-day business, it is recommended to plan API updates when systems’ traffic is at its lowest—e.g., at night or on weekend. An organization may also consider blue-green deployments to ensure zero downtime during upgrades.
Tighten security
To properly secure your infrastructure against vulnerabilities, there are a number of well-established security best practices to follow.
- Perform network audits to identify existing vulnerabilities, open ports, and unnecessary applications.
- Deploy network and security tools, such as firewalls, data loss prevention software, intrusion detection and prevention systems, as well as security information and event management systems.
- Divide the network into different segments to keep each network isolated in case of a security breach, minimizing the impact of any attack.
- TLS encryption can help to secure APIs that are frequently used to exchange sensitive data.
- Adhere to the principle of least privilege, which states that users or processes are granted the minimum required access to perform a function.
- Use authentication and authorization tools, such as OAuth2.0 and OpenID Connect.
- Conduct regular perimeter scans to discover and create an inventory of APIs.
- Set request limits to prevent denial-of-service attacks.
Build microservices
The integration of a KYC platform into an existing legacy system may require taking small steps toward digital transformation. A company may consider breaking its monolith into independent microservices and start this journey with noncritical processes or functionality. An organization needs to constantly monitor its systems to identify bottlenecks. Once a failing process is detected, it can be rewritten as a microservice. This will enable a company to take incremental steps, learn from mistakes, and iterate, minimizing the risk of costly errors.
Additionally, microservices can be written using a variety of programming languages, including Golang, Java, Python, C++, Ruby, Node.js, C#, etc., enabling organizations to rely on existing codebase. (Previously, we’ve written BNY Mellon’s transformation, which involved embracing the microservices paradigm.) Containerization will promote added flexibility, portability across systems, efficient allocation of resources, etc.
Automate monitoring
To improve the detection of money laundering and other financial crime, real-time monitoring of transactions is a must. Monitoring systems should be customizable to allow the creation of business rules. For example, a business rule can trigger validation checks whenever a bank employee updates customer information, such as passport or driver’s license details. In addition to detecting when customer information is changed, monitoring systems should also be able to verify whether regularly timed identity checks (i.e., monthly, quarterly, semiannually, annually, etc.) are working. It is also possible to flag high-risk transactions the same way the Alloy’s platform does, for example.
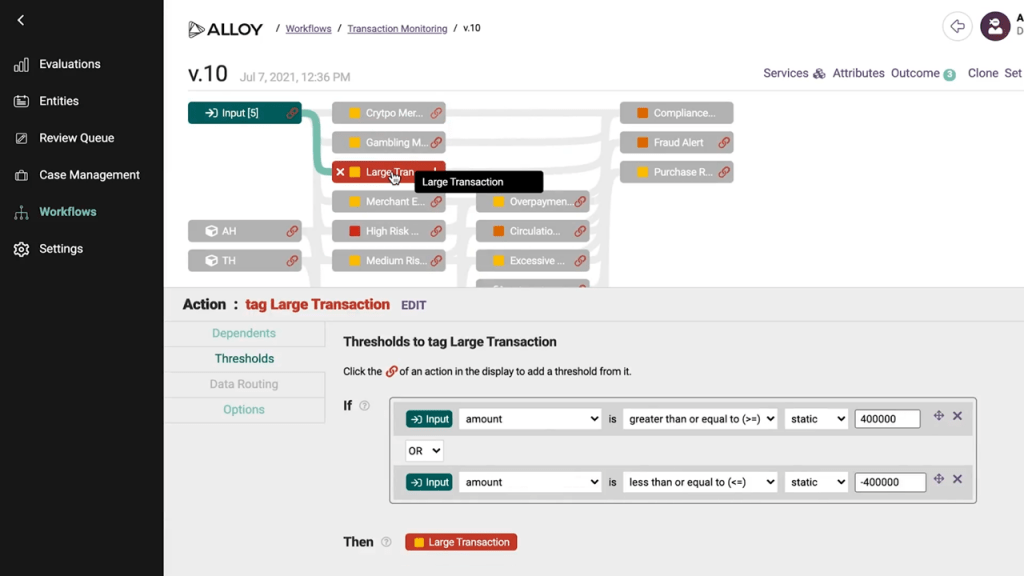 Custom rules for transaction monitoring in Alloy (Image credit)
Custom rules for transaction monitoring in Alloy (Image credit)
Optimize data flows
Companies need to conduct regular performance tests and continuously monitor network traffic to identify sources of bottlenecks. It also helps to segment a network into smaller subnetworks. With segmentation, a company can reduce or increase traffic to individual subnetworks to minimize the load on congested areas. The use of content delivery networks can also decrease response times. Additionally, organizations need to proactively monitor how integration with a KYC platform impacts the latencies of customer-facing and core banking systems.
Consider using big data solutions, such as Apache Kafka, Apache Hadoop, Apache Spark, etc., to build high throughput data pipelines that can scale under the load. Companies dealing with large volumes of unstructured and semistructured data can also build data lakes. Due to a flat architecture, data lakes allow for storing raw information in a single place, while enabling to manage and manipulate disperse data in real time.
Improve data quality
Implementing a good data governance strategy is key to ensuring data quality. Organizations need to put people and processes in place to maintain consistent data. To start, companies can assign data stewards that will be responsible for Master Data Management, data warehousing, as well as other associated techniques and tools.
Digital transformation at the cost of security
The COVID-19 pandemic has drastically changed the way many organizations operate as working remotely has become the new normal. Lockdowns and social distancing restrictions are forcing financial institutions to direct customers to digital channels. According to a report by Deloitte, the pandemic has vastly accelerated digital transformation and the adoption of new technologies in the financial industry.
While there are financial institutions with the necessary resources and in-house development teams to quickly adopt new technologies, other organizations do not have the same luxury. As a result, some banks have eased up on their KYC procedures to accommodate people without valid IDs or transactional account with any financial institution.
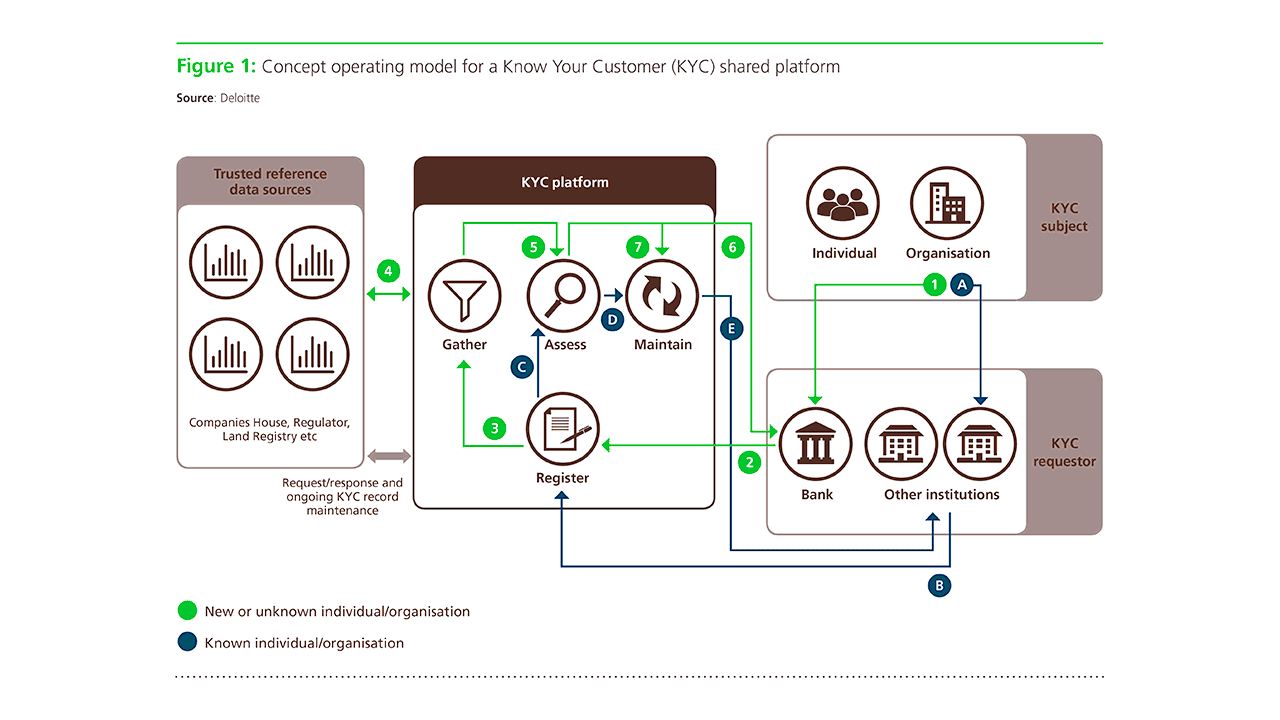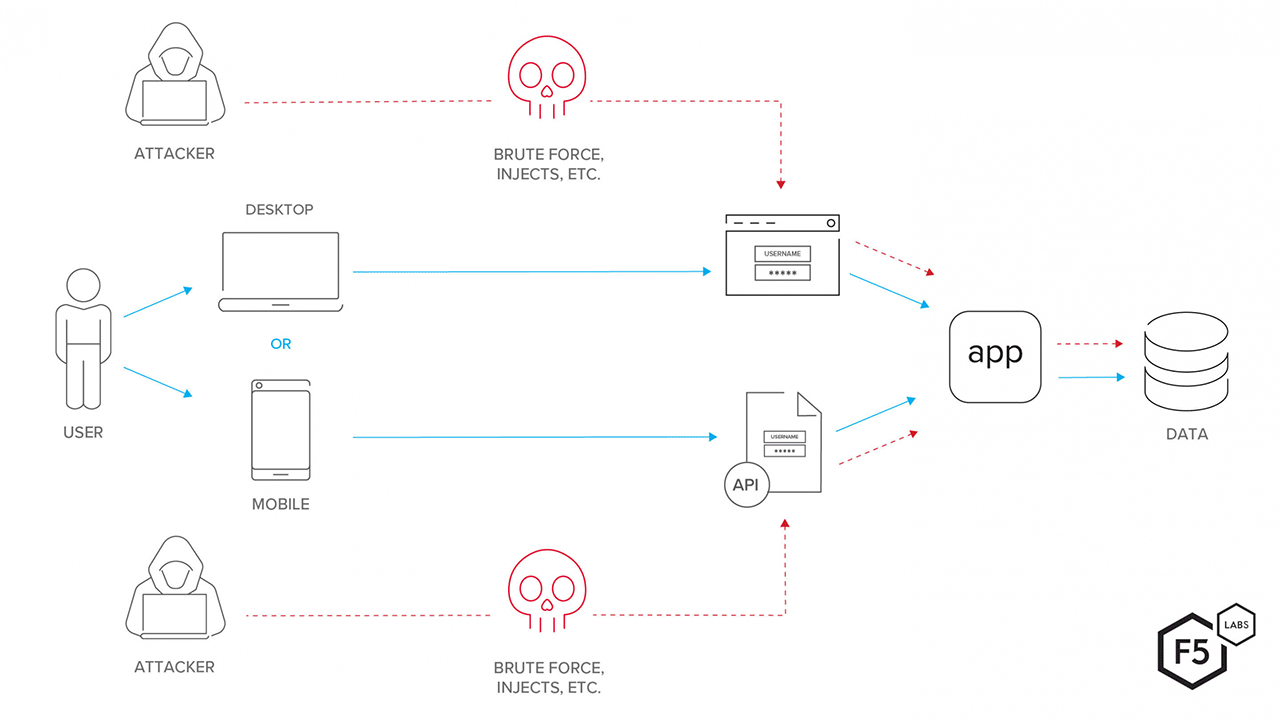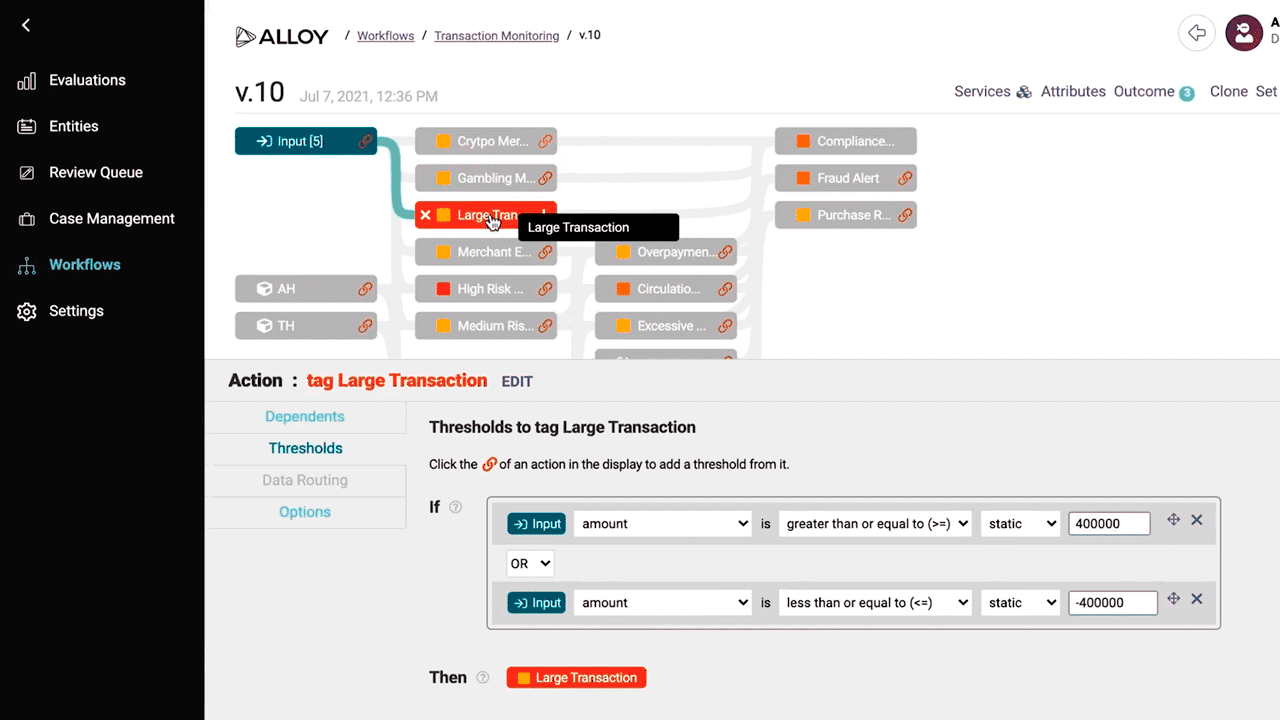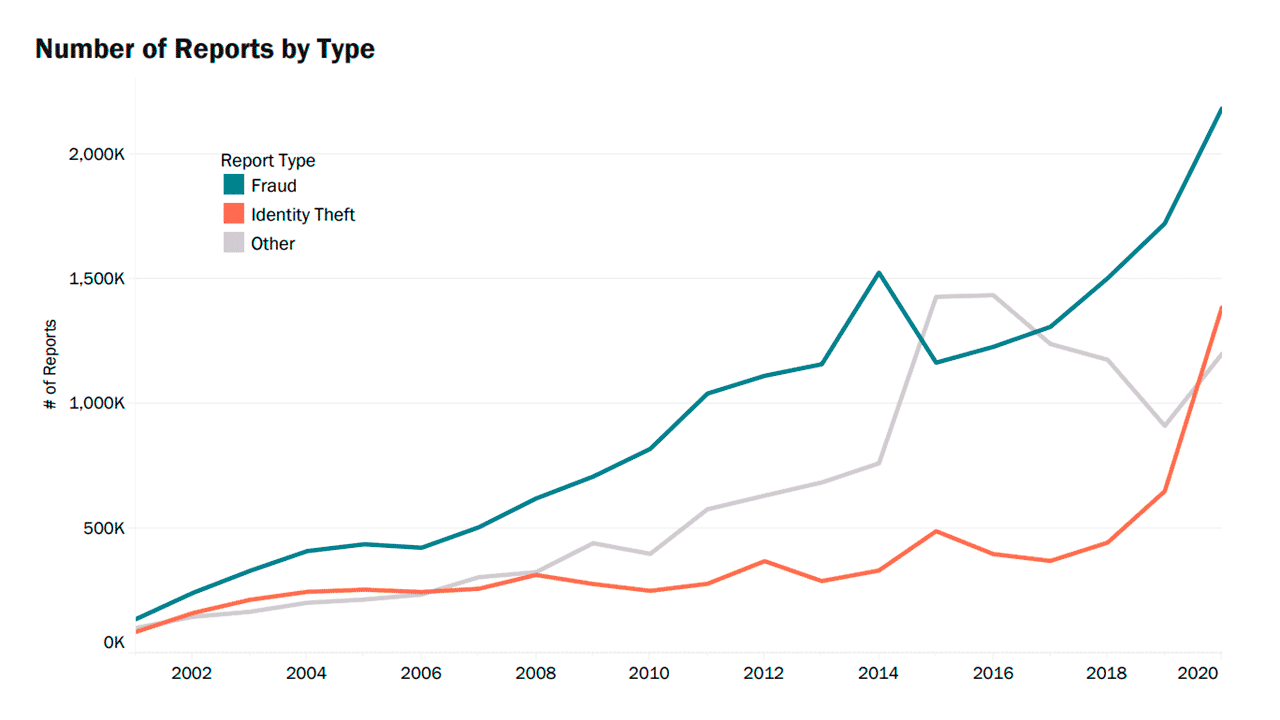
Relaxing KYC processes enables more people to access vital services such as banking, but it also provides criminals with an opportunity to exploit. According to a report by the Federal Trade Commission (FTC), fraudulent activity in the USA increased from 1,723,234 in 2019 to 2,184,531 in 2020. Meanwhile, identity theft increased from 650,523 to 1,387,615.
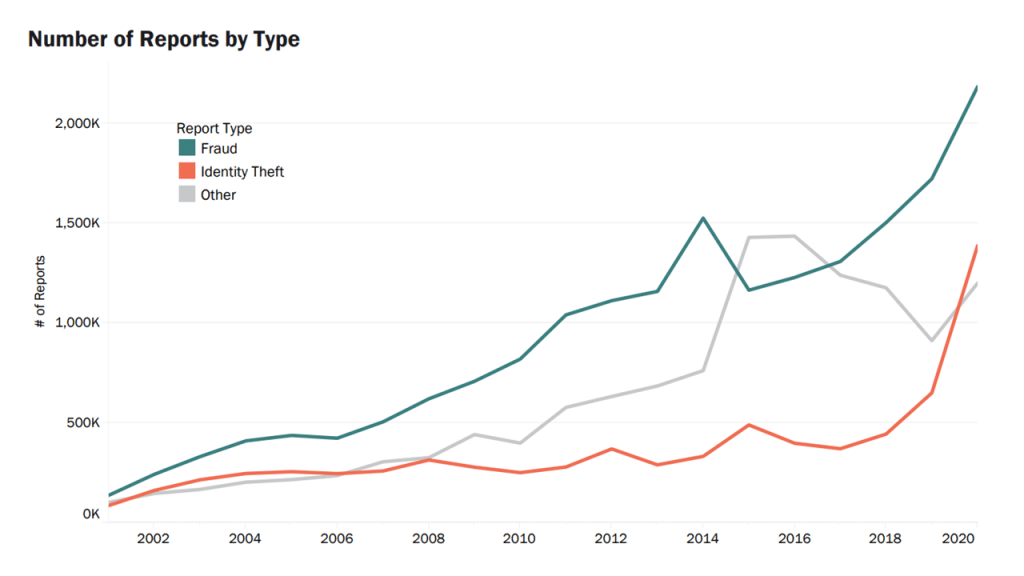 A double increase in identity theft in the USA as of 2020 (Image credit)
A double increase in identity theft in the USA as of 2020 (Image credit)The pandemic has highlighted the need for digital transformation in the financial industry. However, it should not be done at the cost of reduced KYC requirements.
While there is a definite increase in the demand for digitized financial services, banks and other financial institutions should also meet the heightened security and compliance requirements for providing such services. Understanding and overcoming the challenges associated with integrating KYC is a crucial step in financial digital transformation.
Further reading
- Technical Challenges to Address When Integrating Banking as a Service
- Digital Transformation in Banking: New Challenges for a New Era
- Blockchain Can Help Banks to Better Manage the Identity of Customers