Decentralized Blockchain as a Solution to IoT Security
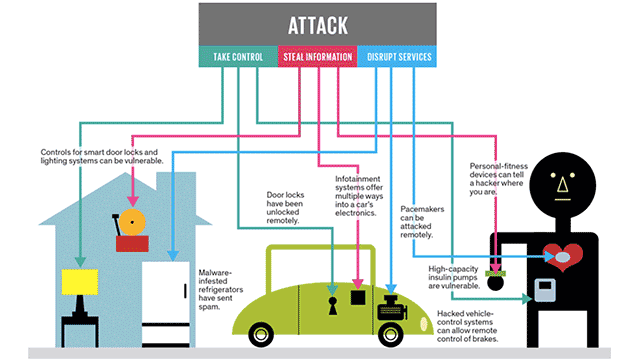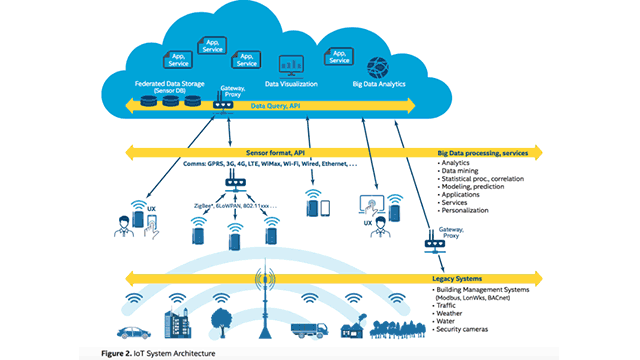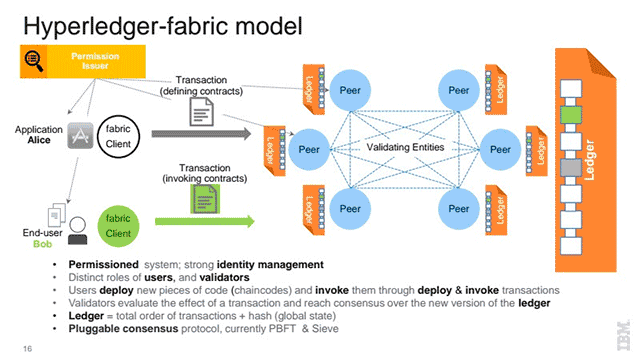
A failure in cybersecurity
On October 21, 2016, popular online services and platforms, such as Amazon, Paypal, and Twitter among several others, became inaccessible for close to 12 hours costing several organizations in lost business. This marks the day of the 2016 Dyn cyberattack, where multiple distributed denial-of-service (DDoS) attacks hit the Domain Name System (DNS) provider—Dyn.
A DDoS attack is accomplished by repeated DNS lookup requests from millions of IP addresses. In the aftermath of that security breach, it was discovered that the malicious attacks were executed through a botnet of Internet of Things (IoT) devices—printers, sensors, gateways, etc.—that had been infected with the Mirai malware.With the continued growth of the IoT across enterprises, security only becomes more important. San Jose State University’s Ahmed Banafa has recently led a webinar exploring the idea of using blockchain as a means of security for the IoT.
Common IoT architecture?
Understanding the different building blocks of IoT, identifying the areas of vulnerability in each block, and exploring technologies needed to counter each of the weaknesses are essential in dealing with security. According to Ahmed, there are four building blocks:
- Things. Defined as uniquely identifiable nodes, primarily sensors, that communicate without human interaction using different connectivity methods.
- Gateways. Act as intermediaries between things and the cloud to provide the necessary connectivity, security, and manageability.
- Network infrastructure. Comprised of routers, aggregators, gateways, repeaters, and other devices that manage the flow of data.
- Cloud infrastructure. Contains large pools of virtualized servers and storage that are networked together with computing and analytical capabilities.
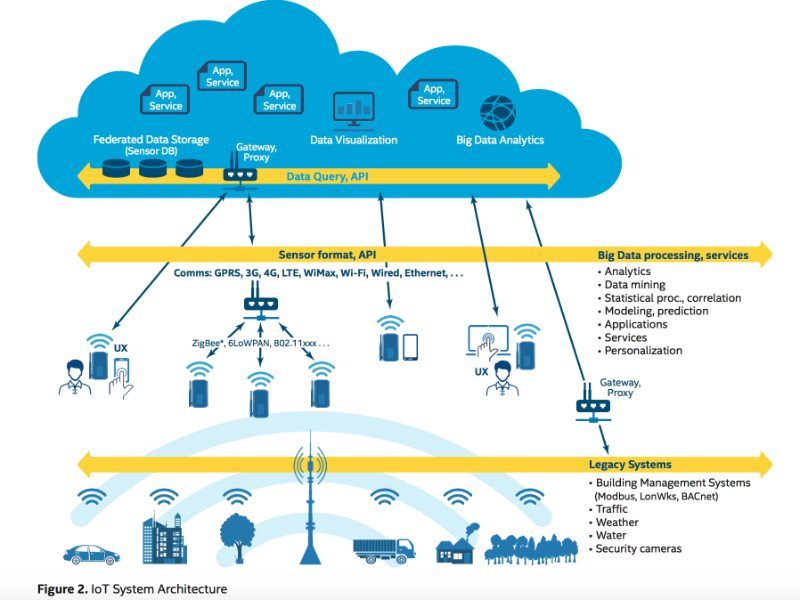 Image credit
Image credit
IoT security challenges
Existing security technologies will play a role in mitigating IoT risks but they are not enough. There are still several challenges to be addressed:
- Design. Simply put, many IoT systems are poorly designed and implemented using diverse protocols and technologies that create complex and sometimes conflicting configurations.
- Maintenance. There is limited guidance for life cycle and management of IoT devices.
- Privacy. The issue of privacy for an IoT device is complex and not always evident.
- Standardization. There is a lack of standards for authentication and authorization of IoT edge devices. Additionally, security standards for platform configurations involving virtualized multi-tenant IoT platforms is immature.
“There is no one single standard used among all the devices in the IoT.” —Ahmed Banafa
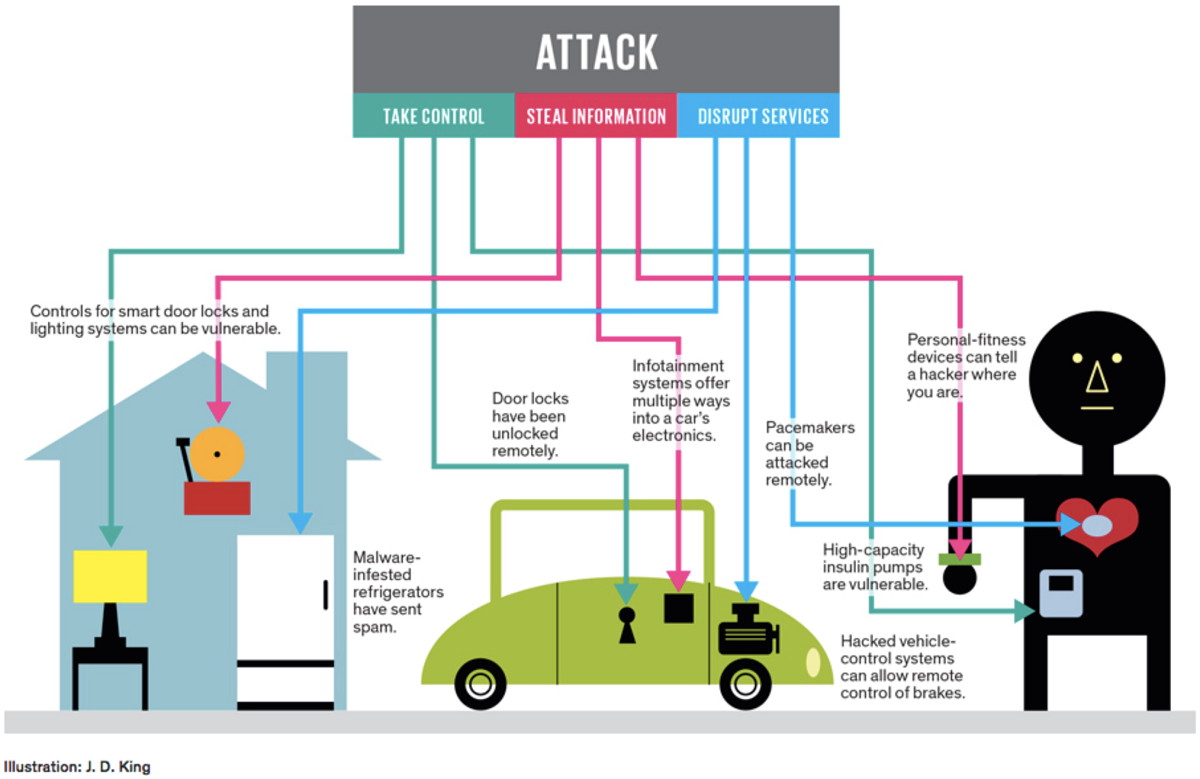 Image credit
Image creditAny new security solution will also have to protect IoT devices and platforms from both informational and physical attacks. These measures should also include a method for encrypting communications and to address new challenges, such as impersonating devices or denial-of-sleep attacks that drain batteries to denial-of-service attacks.
Given all the above, perhaps, one of the greatest challenges in IoT security is that many devices use simple processors and operating systems that may not have the capacity to support new approaches in security.
Changing the architecture
According to Ahmed, most connected devices make use of the server/client model, where IoT ecosystems rely on centralized, brokered communication models. In this system, all devices are identified, authenticated, and connected through cloud servers with huge processing and storage capacities. Connections between devices have to go through the Internet even if they happen to be a few feet apart.
“We still live in the server/client model that we started way back in the 80s and the 70s.”
—Ahmed Banafa
 Image credit
Image creditWhile this model has connected generic computing devices for decades and will continue to support small-scale IoT networks as we see them today, it will not be able to scale up with the challenges already being faced in the IoT. In this regard, adopting a decentralized model could be the way forward.
To perform the functions of traditional IoT solutions without a centralized control, the decentralized approach needs to have three fundamental capabilities:
- Peer-to-peer messaging
- Distributed file sharing
- Autonomous device coordination
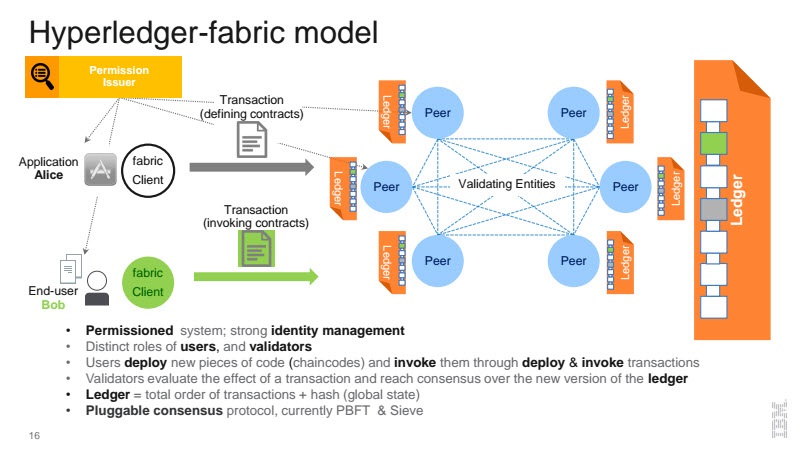
These requirements are conveniently already available in a rapidly growing technology in the blockchain space—Hyperledger.
In a nutshell, a blockchain is a shared, replicated ledger that has consensus, immutability, finality, and provenance. Building on top of this model, Hyperledger Fabric saves computation cycles, scales well, and responds to the multitude of industrial use case requirements by providing a secure, robust model for identity, auditability, and privacy.
Could it work?
At the core, transactions in a blockchain are just about manipulating data of any kind. Using this model, Hyperledger will treat message exchanges between devices similar to financial transactions in a blockchain network. To enable message exchanges, devices will leverage smart contracts, which then model the agreement between the two parties.
Though still considered relatively new, blockchain technology has gone beyond finance use cases. Outside the finance industry, blockchain is being used in identity management and green initiatives.
Clearly blockchain technology is still evolving and with it, the potential for it to be used in new and never before thought of scenarios. Could it address the security challenges in IoT? It’s entirely possible as emphasized by Ahmed that blockchain may be the “silver bullet needed by the IoT industry.”
Want details? Watch the webinar recording.
Related slides
Related reading
- The Good, the Bad, and the Ugly Use of IoT: Who Owns the Data?
- Cybersecurity for the IoT: Issues, Challenges, and Solutions
- Deep Learning for Cybersecurity: Identifying Anomalies and Malicious Traffic