Ignoring Security Harms Data Management
Heterogeneous data as a threat
Ponemon Institute surveyed 870 IT professionals and found “nearly 70% feel that access to their unstructured data by employees is very often unwarranted.” Furthermore, 84% admit this data “is accessible by people with no business need for access.”
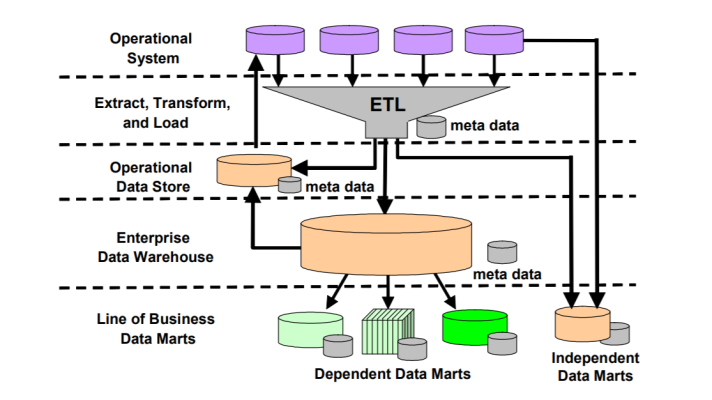
The problem usually lies in the way unstructured data is spread across the organization’s knowledge management systems, corporate applications (CRM / ERP systems), databases, files, etc., and the lack of a clear vision of how it should be consolidated. Recent Gartner research supports this with the figures of as much as 80 percent of actual or potentially mission-critical enterprise information taking the form of unstructured or semi-structured data.
So, you are at the stage where you’ve already realized that your company lives and thrives on data (research, development data, customer private data, contact list, spreadsheets / tables, etc.). You work so hard and do everything you can to keep your data clean and consolidated, and once you finally have the system that delivers quality at hand, you realize that your data isn’t exactly safe. Bummer! Today, when information is as valuable as it is and companies cannot afford having it stolen, lost, or disclosed, information security becomes the critical element and basically the driving force in most business processes.
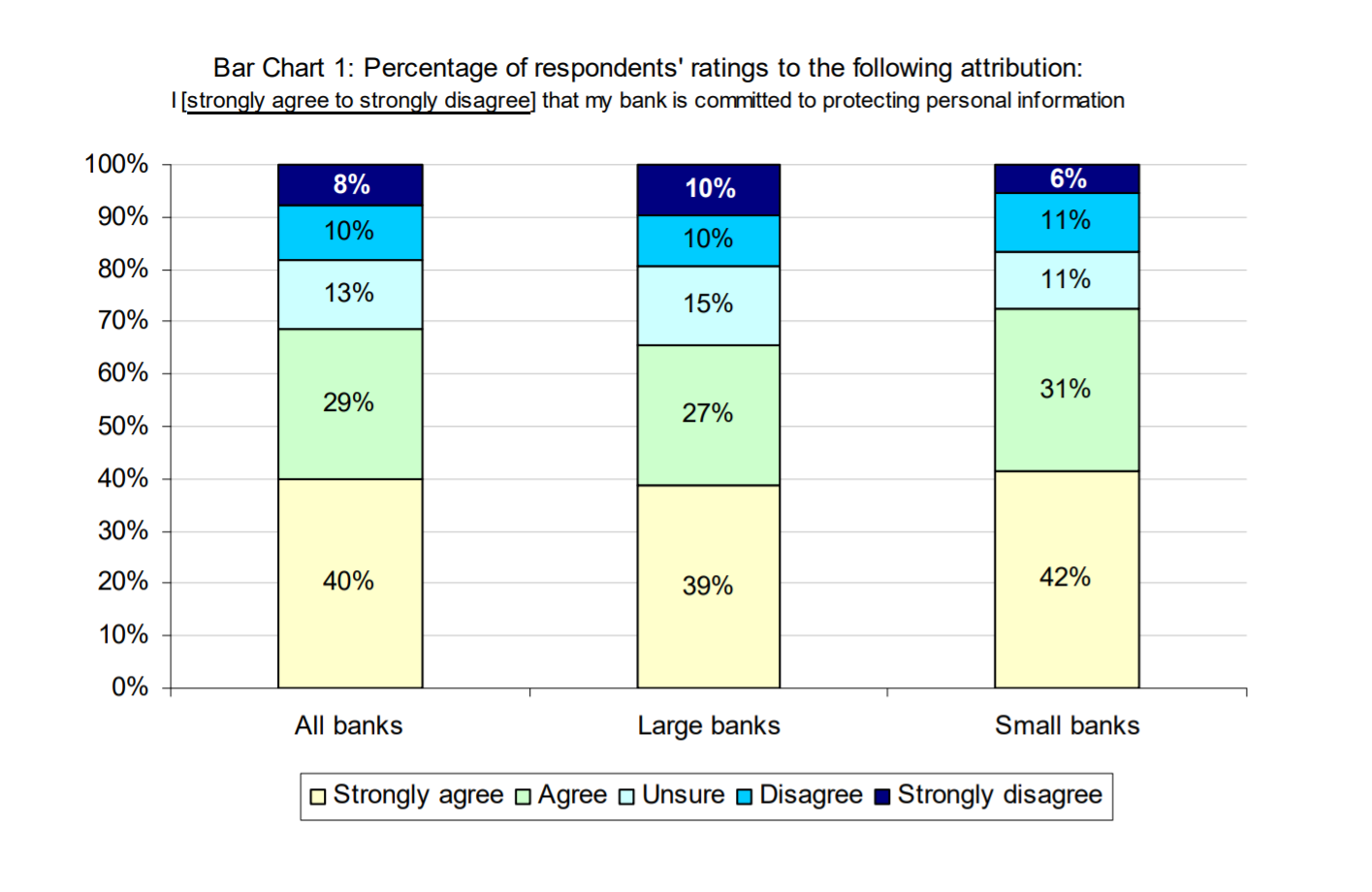
 Source: “State of the Data Integration Market 2008–2009” (Oracle)
Source: “State of the Data Integration Market 2008–2009” (Oracle)
Internal vulnerabilities
All potential threats can be divided into external or internal ones. External threats include unauthorized programs (such as worms, Trojan viruses, spy programs, etc.), and there is really no universal solution that would protect your company from all types of threats, that’s why there are so many specialized tools taking care of each particular problem. However, it’s the internal threats that usually make companies most vulnerable.
A recent Forrester survey of 305 security and e-mail professionals revealed some scary but realistic statistics:
1 in 3 companies investigated a breach of confidential data last year.
1 in 4 companies experienced an “embarrassing” leak of confidential information.
1 in 5 e-mails contains a legal, financial, or regulatory risk.
Here, two of the most probable scenarios of information security violation are:
- the deliberate theft of confidential data by authorized users (or so-called insiders)
- unintentional leak that can be caused by a number of factors (lack of awareness about company’s security policies, for instance)
When creating an information security system, developers try to extend its functionality to the maximum so as it would ensure extensive protection. Even operation systems today contain security features designed to increase an enterprise’s safety level. But this “universality” is unacceptable when speaking of valuable data. A universal security system becomes useless in corporate networks, where internal threats prevail (whether intentionally or not).
Tips to improve data protection
Ways out? Again, an integrated approach.
First of all, would you send your data by post? I loved the way this article by Calum Macleod of Cyber-Ark Software makes a parallel between postal services and data integration. It compares the mail we send via regular post to the data we migrate between applications enterprise-wide.
Come to think of it, data integration market these days is a lot like the postal services market. People don’t feel 100% confident with neither of them, whether it’s something of value you decide to send to your relatives, or it’s your customer data you’re synchronizing with your accounting system. At least, with data integration, you can check to see that the integration tool lives up to your security expectations before using it.
So, consider these tips by Calum Maclead on how to deal with data securely:
1. Do not expose your internal network.
2. Make sure that intermediate storage is secure.
3. Ensure that data at rest is protected.
4. Protection from data deletion, data loss.
5. Protection from data tampering.
6. Auditing and monitoring.
7. End-to-end network protection.
Enable transparency
Finally, improve transparency over tracking the whole data flow. This article on EbizQ.net suggests Data Loss Prevention (DLP) technologies as a way of securing your most valuable asset and achieving transparency through detailed monitoring. Come to think of it, transparency is the key to creating a healthy and productive environment. Even in data integration systems, transparency is a neccessity, allowing you to see where your sensitive data is going, how it’s being transformed and saved, and how secure it is during these transactions. Transparency is another global asset that needs to be integrated into the corporate system of values.
 Tools to address vulnerabilities (Image credit)
Tools to address vulnerabilities (Image credit)You could say, of course, that transparency is just another vague notion (like total security and clean data), perfection hard to achieve, especially for the old market players with established processes. Hard, yes, but not impossible. It’s something to go for. In the end, when your transparency efforts deliver security, it’s your company that will benefit.
So, looks like enhance transparency equals improve security now. Keep in mind, like with anything that has to do with data cleansing, integration, and migration, the right security technology eventually comes in handy.
Further reading
- Top Data Integration Challenges: Meet DQ, CDI, EAI, DW, and BI
- SOA Risk Mitigation
- Unstructured Data: a Challenge for IT Decision-Makers