The Internet of Things to Face Technology, Business, and Social Challenges
Three groups of issues for IoT
The Internet of Things poses the next level of automation for every process in our life. Many companies see big opportunity in IoT because it holds the promise to drive growth by reducing costs, risks, and fraud. Enterprises start to believe that IoT can also enhance customer relations by improving quality, productivity, and reliability within the company.
However, according to Ahmed Banafa of San Jose State University, the future of IoT will be shaped by the three blocks of challenges: technological, business, and societal.
“The technology issues are the most prominent and important, though all the three areas must be addressed for the IoT industry to thrive.” —Ahmed Banafa, San Jose State University
Ahmed urges to think of the future that is soon to come, in which “our very lives and health could become the target of IoT hack attacks.” During a recent webinar, Ahmed focused on discussing all of these topics, suggesting possible “remedies.”
Technology: security comes first
Within technology-driven challenges, Ahmed outlines a set of specific-related issues:
- Security
- Ensuring connectivity
- Compatibility and longevity
- Standards
- Intelligent analysis and actions
Observing that IoT implementation today is challenging by far in many ways, Ahmed stressed the need to consider security as a top priority.
“It is not easy because it’s early days, there’s no unified way of doing it, and you have to bring together many moving parts. Security is the first thing we should do before we think about anything else.” —Ahmed Banafa, San Jose State University
Principles of IoT security
According to Ahmed, today’s sensors are the typical dumb machines we humans usually build, and not at the level of being smart enough to know what’s gong on around them. He also refers to multiple incidents caused by a lack of security.
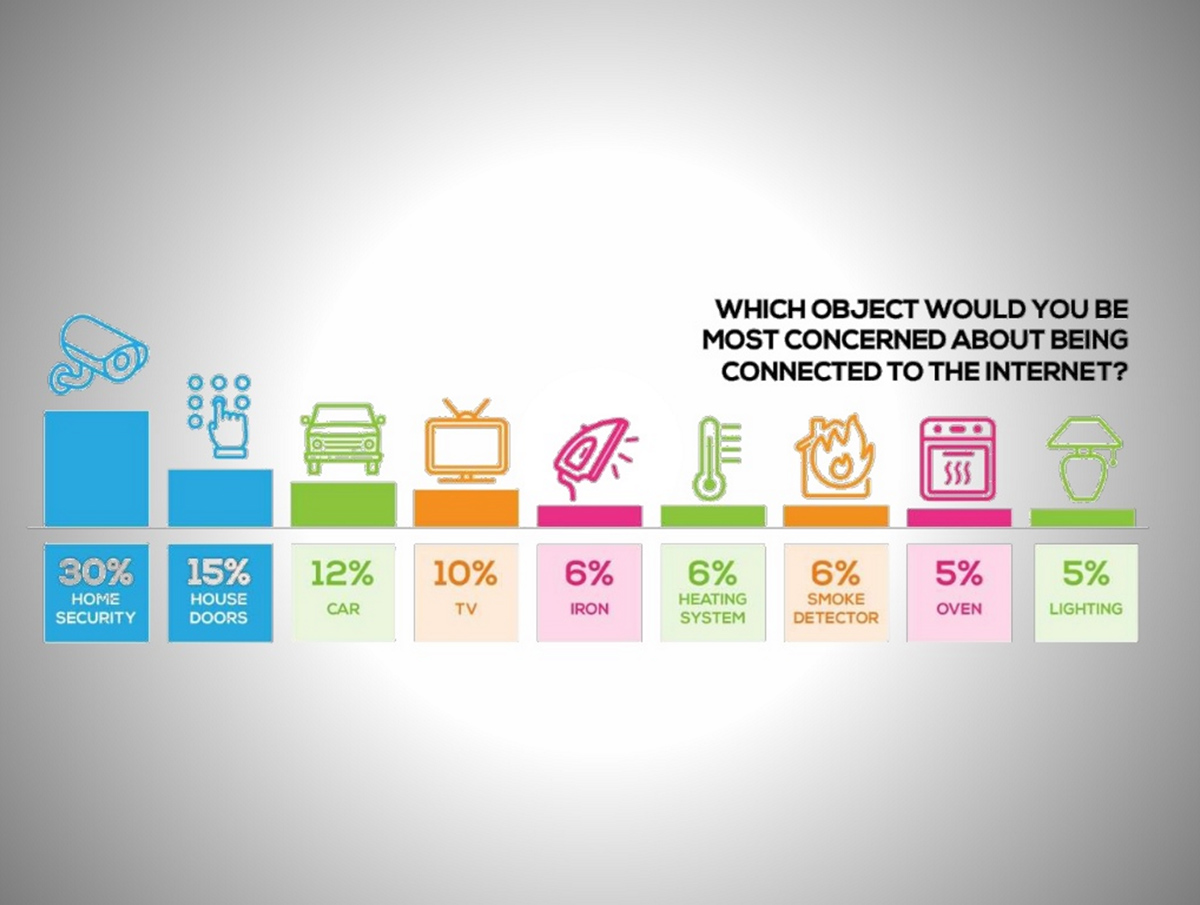
“The IoT has already turned into a serious security concern that has drawn the attention of prominent tech firms and government agencies across the world. (For example,) the hacking of baby monitors, smart fridges, thermostats, drug infusion pumps, cameras, and even assault rifles are signifying a security nightmare being caused by the future of IoT.” —Ahmed Banafa
Ahmed doesn’t see the situation getting any easier to handle. “This fear was of course realized with a massive distributed denial of service attack that crippled the servers of services like Twitter, Netflix , The New York Times, and PayPal across the U.S. on October 21, 2016,” he adds.
“So many new nodes being added to the networks and the Internet will provide malicious actors with innumerable attack vectors and possibilities to carry out their evil deeds, especially since a considerable number of them suffer from security holes.” —Ahmed Banafa
Security-related issues further encompass:
- Undefined audit and logging standards for IoT components
- Restricted interfaces for IoT devices to interact with security devices and applications
- No focus on identifying methods for achieving situational awareness of the security posture of an organization’s IoT assets
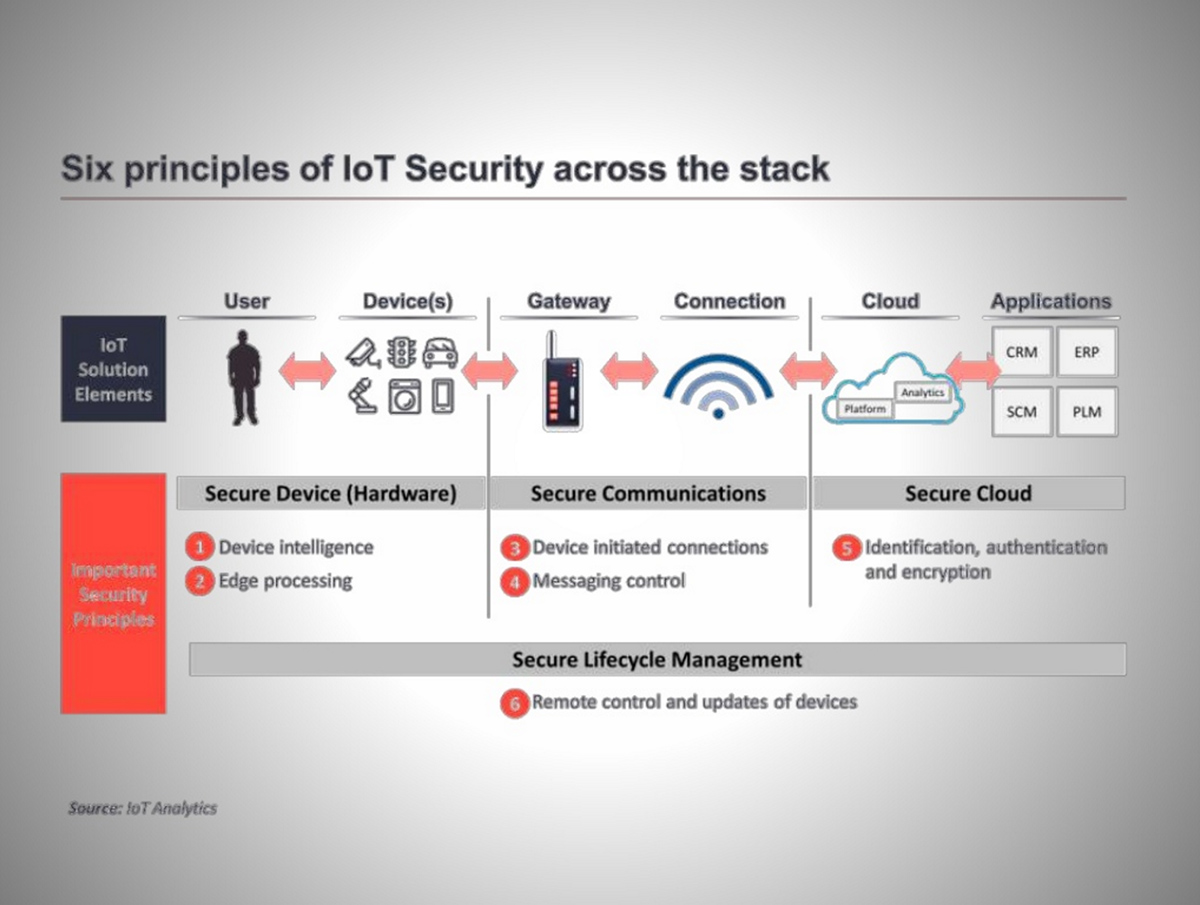
Enterprises can remedy security concerns by considering six major security principles across the stack:
- Device intelligence
- Edge processing
- Device initiated connections
- Messaging control
- Identification, authentication, and encryption
- Remote control and updates of devices
Ahmed recommends that vendors move beyond the present “gold rush” era of the IoT, in which security is taking a back seat to functionality in a mad dash for customers.
Connectivity and decentralization
As devices grow in number at the speed of light, ensuring connectivity is a thing to think about now, as it will define the communication models and the technologies behind. According to Ahmed, today, we yet stick to the centralized, server/client paradigm to authenticate, authorize, and connect different nodes in a network. This approach is still a working one, but soon it hardly will.
“This model is sufficient for current IoT ecosystems, where tens, hundreds, or even thousands of devices are involved. But when networks grow to join billions and hundreds of billions of devices, centralized brokered systems will turn into a bottleneck.” —Ahmed Banafa, San Jose State University
As one would expect, building complex systems like that will require huge investments to maintain cloud servers that can handle such large amounts of information exchange. An entire system can go down if the server becomes unavailable.
So, Ahmed stressed the need for a rigorously decentralized approach to compute within growing IoT networks. This touches on the idea of fog computing (a term coined by Cisco), also known as edge computing.
As enormous numbers of sensors are deployed over wide areas, Ahmed rhetorically asked why we had to send this data all the way to the cloud. According to him, part of the task can be accomplished by moving functionality to the edge, in which such smart devices as IoT hubs take charge of time-critical operations, while cloud servers take on data gathering and analytical responsibilities.
Ahmed also mentioned the notions of peer-to-peer communications, in which devices identify and authenticate one another, leading to “meshes with (the added benefit of) no single point of failure.” This approach introduces its own chellenges, of course, but they can be addressed with new technologies, such as blockchain, according to Ahmed.
Compatibility and standards
All of these issues only increase the challenge of having established standards and protocols and some semblance of order in their use. However, standards and protocols are a mess.
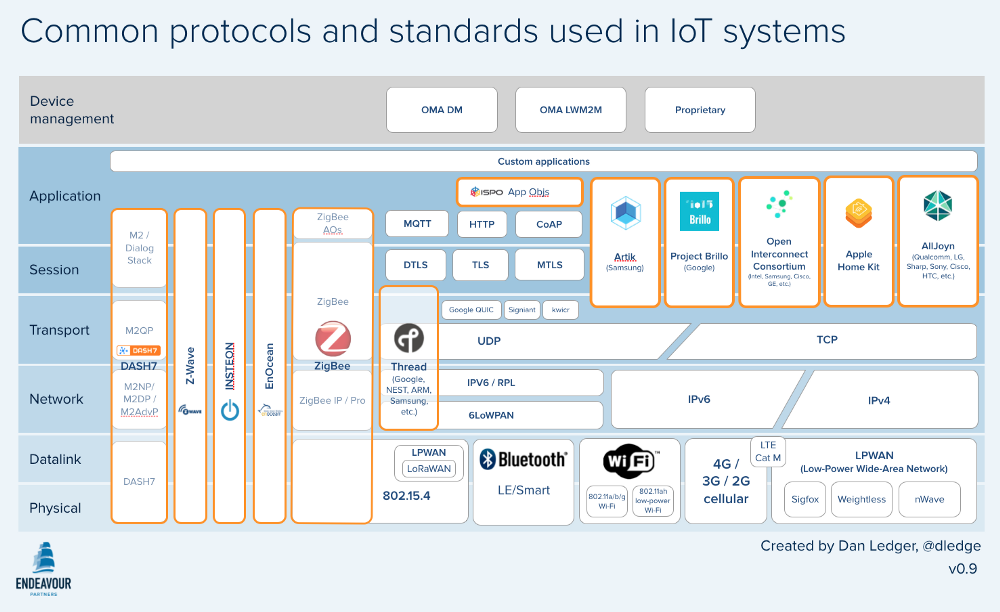 Source
Source“The IoT is growing in many different directions, with many different technologies competing to become the standard. This will cause difficulties and require the deployment of extra hardware and software when connecting devices.” —Ahmed Banafa, San Jose State University
Issues with Wi-Fi while capturing data are becoming more relevant, as well. Ahmed provided an example of Tesla, which strives to capture a lot of data in real time and close to real time. Information about brakes, for example, needs to be transmitted quickly and consistently, but faces unacceptable lags in today’s 4G LTE networks. Ahmed said the deployment of 5G networks should remedy this particular issue and issues related to it.
We should note, however, that there is no consensus standard for 5G (sounds familiar). 5G networks are not likely to roll out before 2020 and their promised blazing speeds (100 Mbps to 1 Gbps) are only part of the equation in making them effective with, say, connected cars in motion.
Intelligent analysis and actions
Ahmed noted that “the last stage in IoT implementation is extracting insights from data for analysis, where analysis is driven by cognitive technologies and the accompanying models that facilitate their use.” According to him, timely decision-making and action should rely on real-time event processing and moden analytics tools. Still, he balanced this thought with the reality that legacy systems in most enterprises were built to handle structured data.
“Traditional analytics software generally works on batch-oriented processing.”
—Ahmed Banafa, San Jose State University
The new world of unstructured data maelstroms will need new systems, he thus implied. These new systems must be working with ever-improving algorithms because “without smart algorithms, we’ll just be working with more dumb systems.”
Business: the need for an IoT strategy
All of the technical issues lead to a business-related conclusion: “without a sound and a solid business model for IoT, we will have another bubble,” according to Ahmed. “This model must satisfy all the requirements for all kinds of e-commerce: vertical markets, horizontal markets, and consumer markets,” in an environment of regulatory and legal scrutiny.
To achieve that, enterprises have to clearly understand the value chain and business model for solutions in each of the IoT sectors:
- consumer (smart cars, phones, watches, etc.)
- commercial (e.g., inventory control or medical devices)
- industrial (i.e., connected meters, pipeline monitors, and robots)
Some insight for an IoT strategy can be found in a survey from BI Intelligence that Ahmed cited during the webinar, in which business leaders listed their reasons for adopting IoT-based solutions.
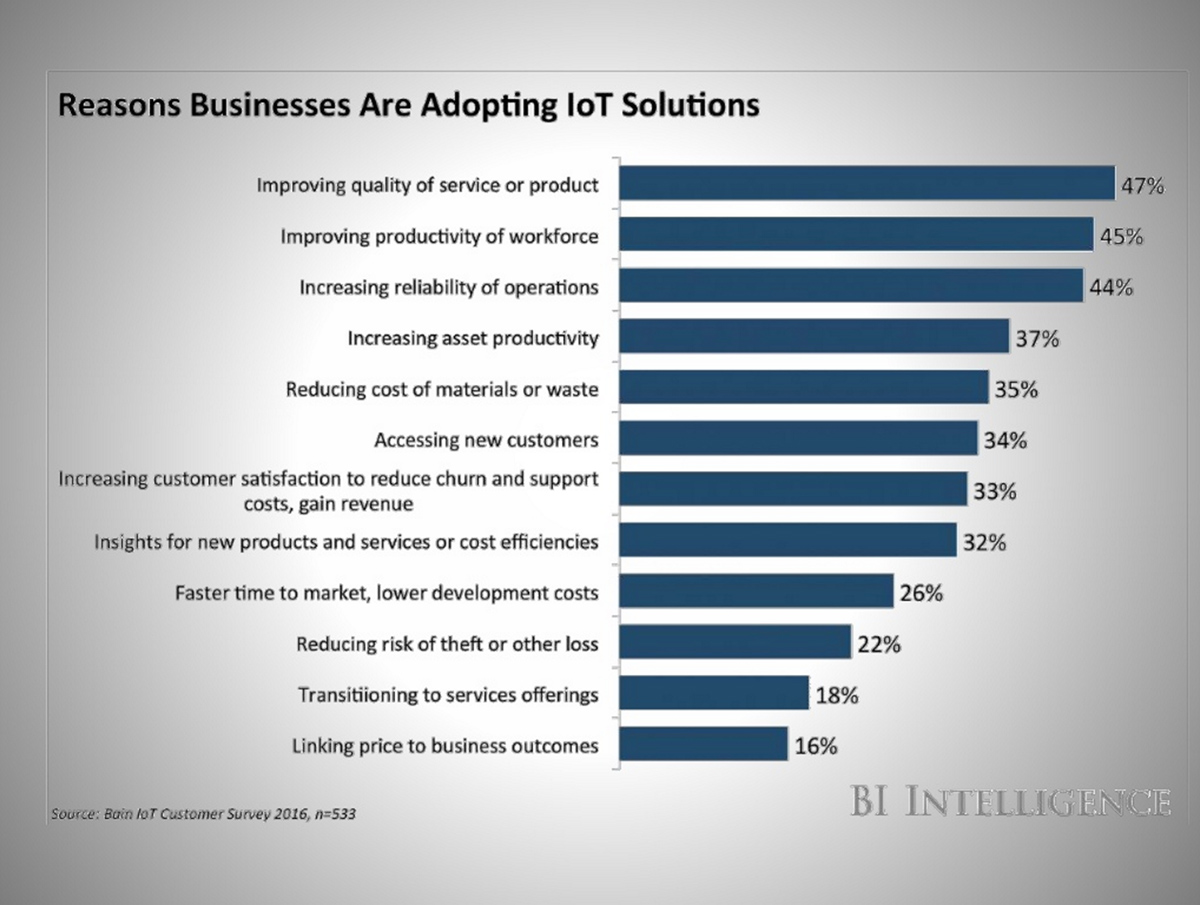 Source
SourceA successful IoT strategy should address as many of these as possible.
Society: privacy issues and regilations
The third leg of the IoT stool comprises societal concerns, Ahmed said. Not only do “customer demands and requirements change constantly,” he said, but the uses for IoT around the globe are also expanding and changing, crossing social and cultural boundaries.
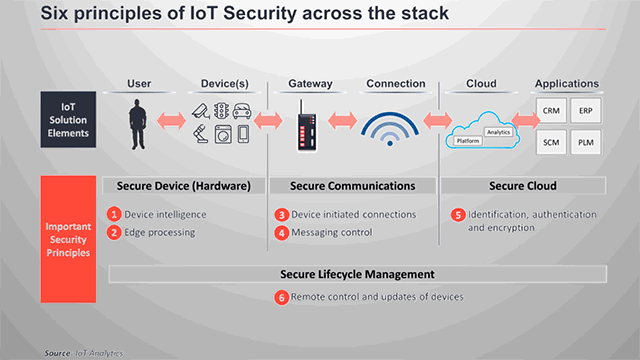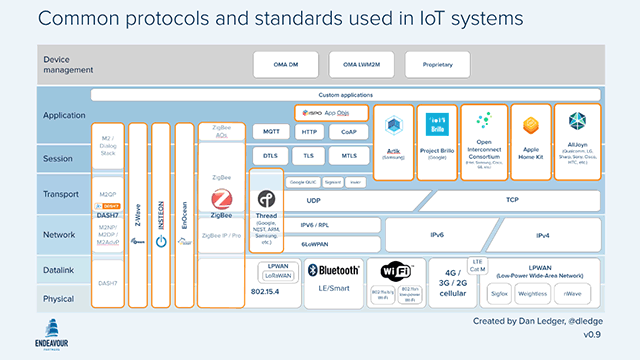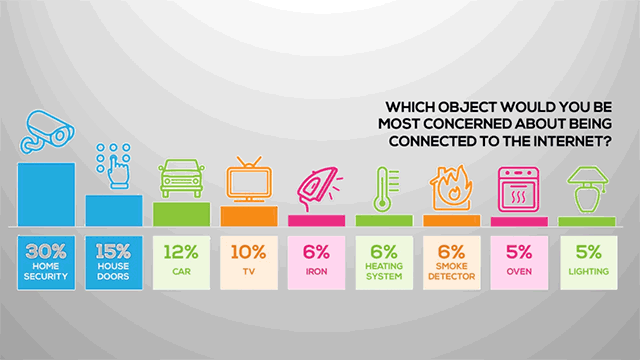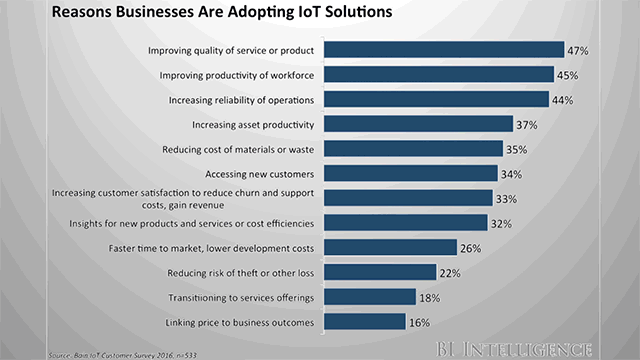
At the same time, lagging or waning consumer confidence for connected products “would prevent the IoT from fulfilling its true potential,” Ahmed said. Here, steps in the need to teach consumers IoT best practices in order to nourish confidence in using connected devices and understanding why they even bought them.
Pesky privacy issues will also not go away, typified by the evergreen question of “who gets access to data and how that data are used to develop products or services and sold to advertisers and third parties,” Ahmed said. He concluded with a thought that we are in great need for “clear guidelines on the retention, use, and security of data, including metadata.”
Want details? Watch the webinar recording!
Related slides
Related reading
- The Good, the Bad, and the Ugly Use of IoT: Who Owns the Data?
- Applying Data-Centric Approach to Unify IoT Security Policies
- Decentralized Blockchain as a Solution to IoT Security
- 2016–2017 Trends: Smart Cities