A New Cloud Foundry Container Engine for Linux, Garden-runC v1.0, Is Out!
On October 17, the new Cloud Foundry container runtime for Linux, called Garden-runC, has been announced by the project leader Julian Friedman (aka Dr. Julz).
The v1.0 version is based on the Open Container Initiative (OCI) spec and replaces the code that’s been used for a couple of years.
The previous Linux back end, Garden-Linux, has reached the end-of-life status, according to Dr. Julz. The team “will no longer be developing new features for Garden-Linux or accepting pull requests from this point.” The support for the legacy Linux back end will be suspended on October 28, 2016.
In with the new, out with the old
“At this point, Garden-runC has been successfully running 100% of the production traffic on PWS for around a month (it has been running a smaller portion of the load for a longer time as we gained confidence),” according to a statement from Dr. Julz published within the cf-list community.
“The Diego team has been testing with and listing compatible releases of both Garden-Linux and Garden-runC for several months. It has also been the only supported Linux back end for Concourse for several months, thereby being used in a broad range of environments and deployment scenarios. In all cases it has held up remarkably well.” —Julian Friedman, IBM
He outlined some specific benefits of the new release (in addition to its following the OCI spec and being a community project) as follows:
“AppArmor is configured and enforced by default and out of the box for all unprivileged containers.
Seccomp whitelisting is used to restrict the set of system calls a container can access, hugely reducing the surface area for break-out exploits. Again, this is set up out of the box, you don’t need to do anything.
The team has been able to simplify and modularize the Garden code base extensively as part of this transition, allowing pluggable networking and rootfs management. This enables (and will be required by) the fast-developing container-to-container networking work and the new “grootfs” OCI-compliant rootfs downloader.
Garden-runC uses the exact same low-level container execution code as Docker/Kubernetes for running containers; so, when you run container images, you know they run identically in Cloud Foundry as elsewhere.”
The Garden team within the overall Cloud Foundry development project has engineers from IBM, Pivotal, and SAP. The project’s tracker sheds some light on the next steps in the development process.
Garden view
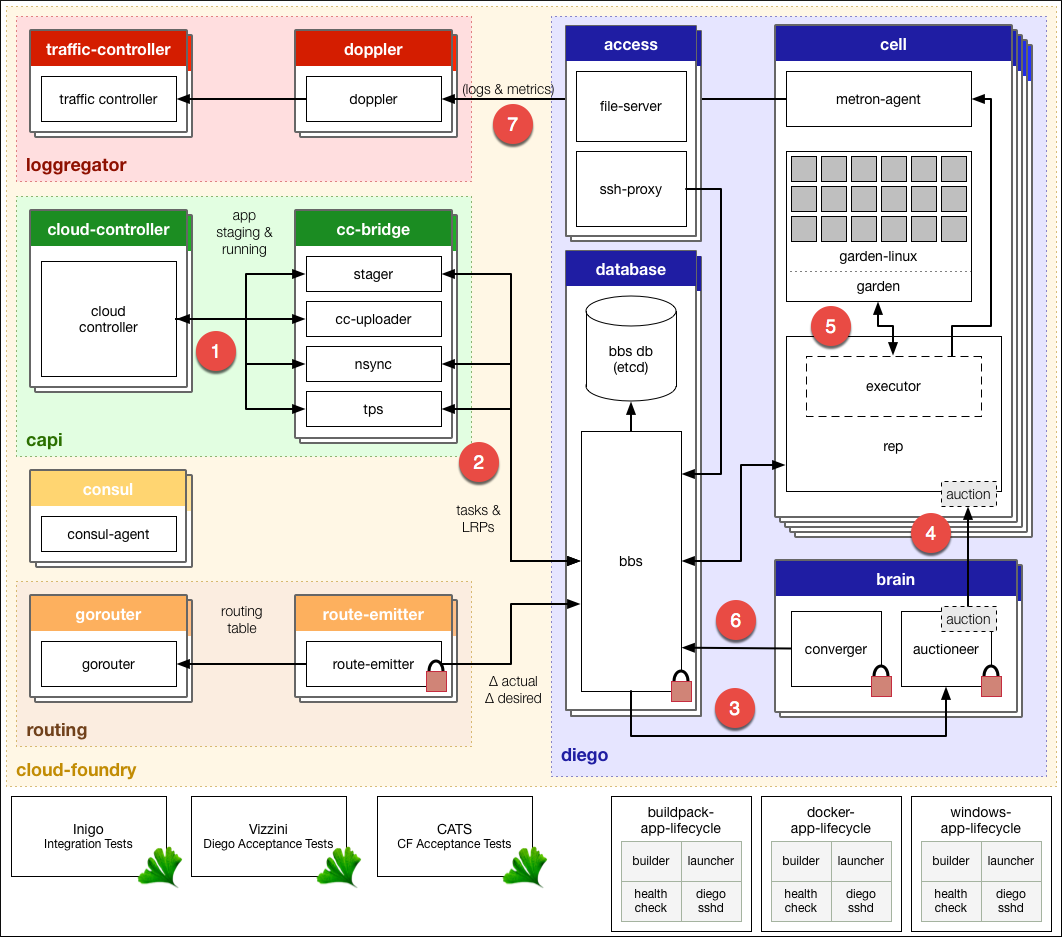
Garden is a containerization layer used by Diego (which itself is set for a final release any day now). It provides a platform-neutral, lightweight container abstraction that can be backed by multiple back ends. One of the great features of the new Garden Linux back end is the possibility to run Docker images. Read our post on Garden internals (a shell, file system, networking, etc.) for the technical details.
Here’s the Diego architecture taken from Cloud Foundry docs—featuring Garden:
According to Dr. Julz, Garden is an “unopinionated” container system, leaving opinionation to higher levels, such as Docker’s highly opinionated environment.
“We like to have the opinionation happen at the higher levels (i.e., in Diego). Because runC follows the OCI spec, it follows that Cloud Foundry will be running the same code as Docker with the use of open containers.” —Julian Friedman, IBM
Last year, Dr. Julz wrote about a couple of advantages:
- “Firstly, it lets us reuse some awesome code and be part of the Open Container community.
- Secondly, it means Cloud Foundry applications will be using not only the same kernel primitives as Docker apps (as they already are today), but also the exact same runtime container engine. This will minimize incompatibility for our Docker life cycle and result in a first-class experience for users, as well as letting us reuse and contribute back to a great open-source code base.”
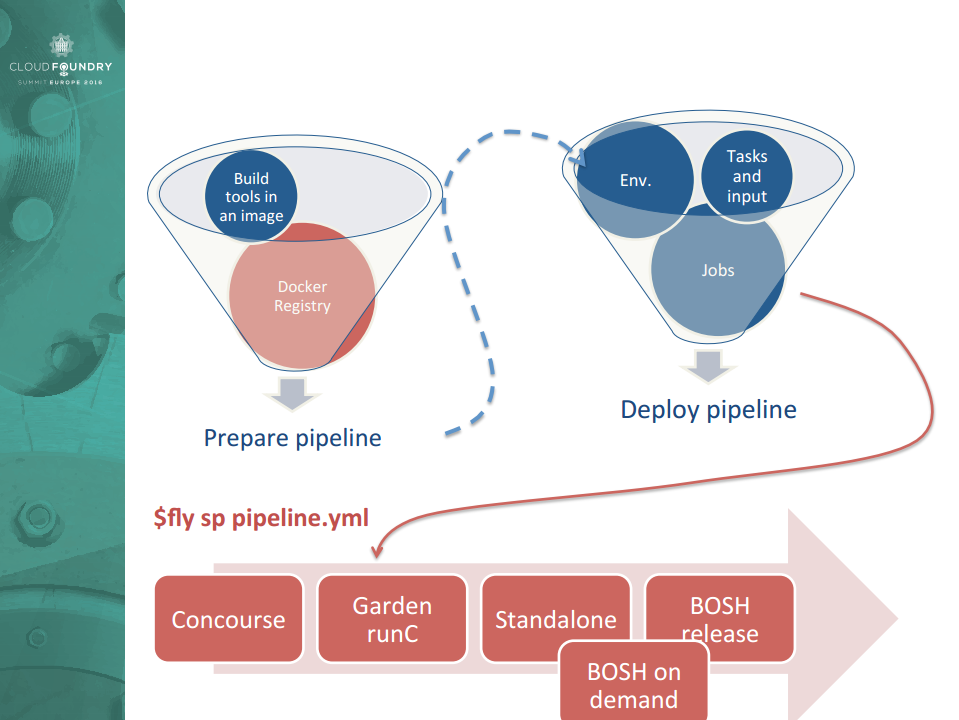
In addition to running apps in Docker containers, using Garden-runC together with Concourse CI enables another interesting possibility. It allows for running the pipeline as a container—with a clear environment and build tools—anywhere and anytime. (The presentation delivered by Alexandre Vasseur of Pivotal a month ago elaborates on this scenario.)
So, the Garden-runC release, obviously, is an important milestone for the Cloud Foundry community—in many ways.
More info on the topic
To dig deeper into the announcement, check out these relevant resources:
- Garden-runC v1.0.0 release
- A public Pivotal Tracker for the Garden project
- OCI Runtime Specification
- RunC container CLI tools
- Cloud Foundry Containers: The Difference Between Warden, Docker, and Garden