Cybersecurity for the IoT: Issues, Challenges, and Solutions
Security was the key topic during a recent Predix meetup sponsored by Altoros in Boston. Speaker Mike Anderson, Chief Scientist of the PTR Group, outlined several dimensions of security along IoT deployments, specific challenges inherent to different types of devices, and how to reduce a deployment’s “attack surface.”
Saving millions of dollars for power plants
Mike was preceded by Mina Botros, a Senior Software Engineer with GE Digital, who gave an overview of the challenges and drivers of the Industrial Internet. After that, Himaja Vadaga, a graduate student at Northeastern University, described an industrial project she’s working on using analytics in GE Predix.
Mina Botros provided a general outline of GE Predix and how developers and organizations can start working with it. He answered several questions concerning its use during IoT deployments, including one about scalability (to which he noted that Predix is based on Cloud Foundry and thus gets its scalability from the platform). As always, predix.io was mentioned as great place to start for people and companies who wish to get involved with Predix.
Himaja Vadaga described a recent project she undertook in which she collected data from equipment and conditions within power plants. She is working to demonstrate potential cost savings in the millions of dollars for a major facility, while also providing insight on building new-generation plants.
Globally, power plants produce more than two terawatts (two million megawatts) around the clock, a number that should grow dramatically as the developing world continues to grow economically.
More devices means more threats
Mike Anderson proceeded to terrify the audience as he outlined the many challenges of data security within IoT deployments.
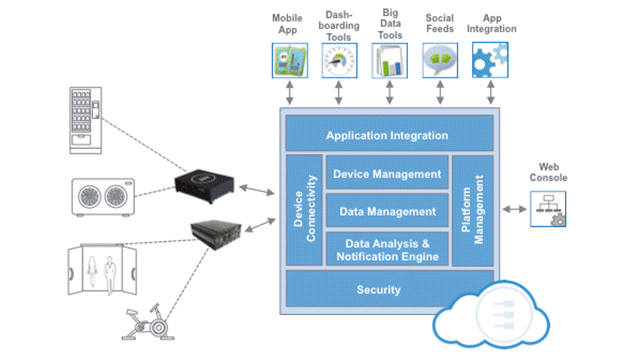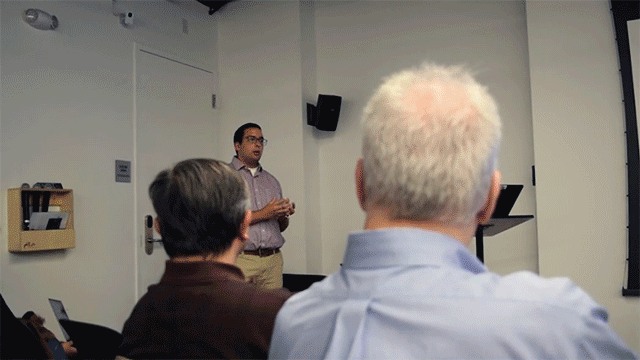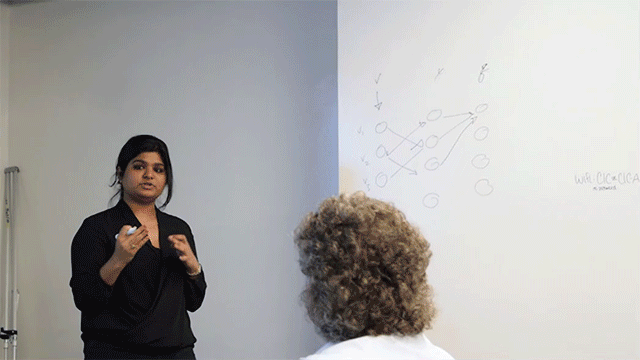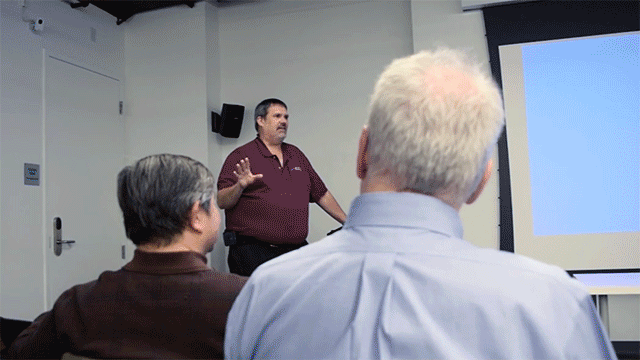
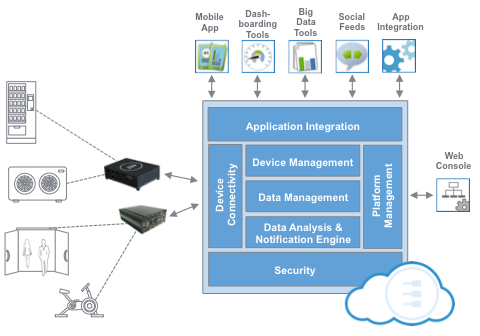
“If your cloud is connected to your sensor, then your sensor is connected to your cloud,” he said, noting that deploying myriad sensors produces an equal number of potential security breach points. He outlined a “fog” model in which sensors first communicate to a border gateway, thus literally shielding cloud-computing infrastructure from raw sensor input.
“We can think of the IoT as being comprised of devices on the edge, middle box, and cloud portions of the ecosystem,” he said. “Edge devices are where the sensors and actuators are found. They are often battery-operated devices with low-power networks.
“The middle boxes are better known as border routers/gateways,” he said. “They use standard Internet protocol (whether IPv4 or IPv6), and may provide data pre-processing. The cloud portion of the infrastructure provides connectivity to external controllers, such as smartphones, tablets, etc.”
“The definition of security varies depending on the audience. For some, it means having locks, alarms and guards as in physical security. For others, it is all about protection from outside hackers as in cybersecurity.” —Mike Anderson, PTR Group
A host of actors are waiting out there to attack anything with a presence in cyberspace, as we all know. Mike grouped them into three broad categories, ranging from amateur hackers (whom he called “script kiddies”), to a range of professional hackers from blackhats to whitehats (hired to try to find potential security flaws) to the world of in-between grayhats, to state-sponsored actors (whom he described as far the most dangerous of all).
Source: eurotech.com
“These state-sponsored bad actors are often blackhats who are paid by governments to find and obtain classified information, conduct industrial espionage, or launch coordinated cyber-attacks,” he said.
“Your own employees are often the number one threat to your security.”
—Mike Anderson, PTR Group
Top 3 security issues
Mike provided the nice acronym “CIA” to describe what he called “The Big Three” issues of security: confidentiality, integrity, and authentication. He noted that authorization and non-repudiation need to be considered as well.
Confidentiality. “One of the easiest characteristics of security to understand,” according to Mike. “The goal of confidentiality is simply that no unauthorized individuals can read the data you want protected.”
A breakdown of data categories includes data-in-flight, data-at-rest, data-in-use, data in the form of message traffic transiting your connections, data-like encryption keys and certificates stored on your system, and temporary use of decrypted keys or certificates in RAM.
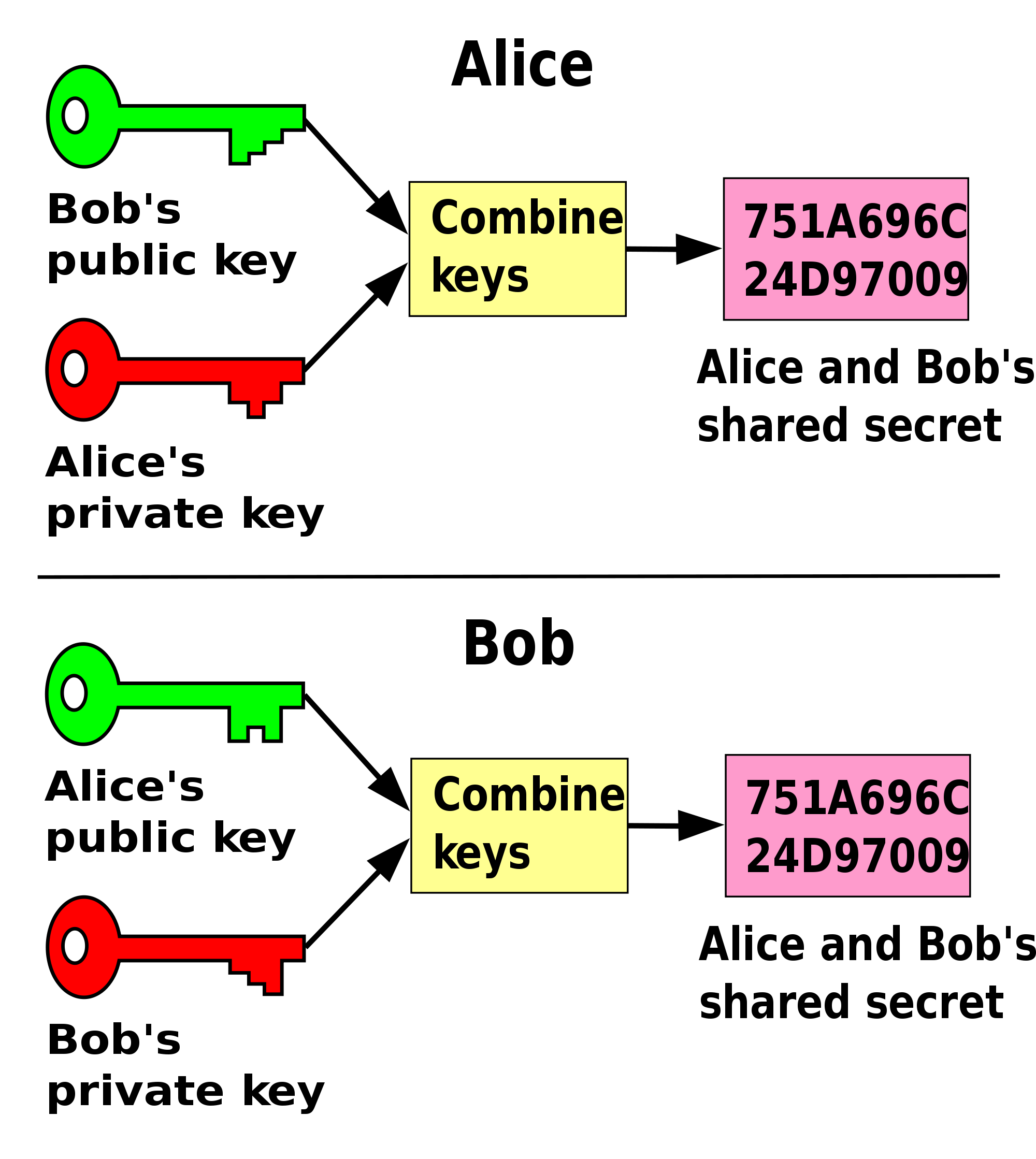
He described both symmetric and asymmetric encryption. Symmetric encryption “has a pre-shared key that must be known on both sides,” he said, e.g., AES, DES, Twofish, Rijndael, and Triple-DES. Asymmetric encryption has public and private keys “and is often referred to as public-key cryptography,” he said, e.g., Diffie-Hellman, RSA, and elliptic curve encryption.
Source: Wikipedia
Integrity. “This encompasses a couple of different concepts,” he said, “system integrity and message integrity. System integrity can be addressed initially by ensuring a secure boot cycle. (With) message integrity, we need to concern ourselves that the message was delivered intact and was not modified.”
Authentication. “This addresses being able to associate the origin of a message, user, or file to a valid source,” Mike said. Single-factor authentication uses a single characteristic to grant access. Examples are passwords, biometrics, PINs, and security tokens. More secure, two-factor authentication combines two factor, such as a fingerprint and drawn pattern or iris scan, along with a security token such as a smart card.
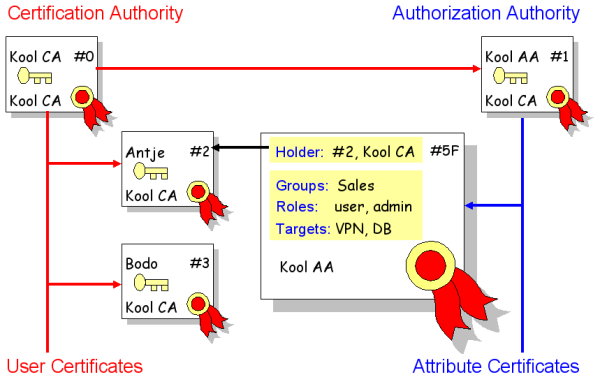
Certificates also come into play, he noted, and are closely tied to the asymmetric encryption approach. “Certificates are a way of binding a particular public key to a specific distinguished name or its alternative, such as an e-mail address or DNS entry,” he said.
Source: free-it.org
Moving on, he first noted that “authorization is more difficult to pin down (and) is related to the system’s access control policies. It’s assumed that a user or system is authorized if they have valid credentials for the platform, a secret key, or knowledge of some private characteristic of the system such as a hidden SSID in a wireless network.”
Then he spoke a bit about non-repudiation, “something that most people don’t think about. Non-repudiation means someone not being able to deny that they sent the message, and is often associated with having the private secret needed to encrypt/decrypt a cryptographically sealed message,” he said.
The challenges associated with devices
When applying all of these core principles to IoT deployments involving Cloud Foundry and Predix, Mike said that all of those edge devices “represent a special set of problems,” as follows:
- They might not always be powered on.
- They often won’t have a main memory unit (MMU) or be able to run an OS.
- They can be easily accessible by unauthorized personnel.
- They have low RAM and low CPU performance.
- Their only connectivity may be wireless.
All of these factors complicate encryption, and “it is difficult to provision every sensor without physically touching every one,” he noted.
Therefore, “do not allow your edge devices to be visible on the Internet, and try to make the devices as dumb and as throwaway as possible, in general,” he said. “They are often simply replaced rather than repaired.”
To paraphrase the late Carl Sagan, there will be billions of devices in our universe very soon, and now’s the time to think about how to protect them and the data they transmit from all of the bad actors in the world.
Want details? Watch the video!
Table of Contents
|
These are the slides from the meetup.
Further reading
- GE Predix and the DDS Standard Transform Healthcare, Control Robots
- Going Loco with GE Predix and Siemens Analytics
- Cloud Foundry and IoT Concerns: The Need for Standardization and Transaction Authentication
About the experts














