How Hyperledger Fabric Delivers Security to Enterprise Blockchain
Examining security
In her session, Elli Androulaki with IBM Research Zurich reiterated the point that blockchains are simply decentralized ledgers that have uniquely trusted ways of establishing the validity and security of transactions. As blockchains’ popularity steadily increased in the past few years, she noted that many types of businesses have developed an interest in them, market valuations (especially Bitcoin) have reached into the billions of dollars, and ecosystems are starting to be created around them.
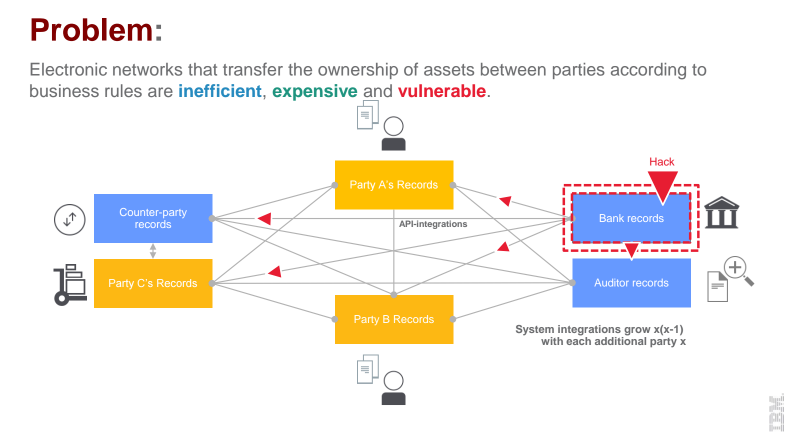
When exploring blockchain adoption within enterprises, she highlighted the need to remove slow, cumbersome, expensive middle steps (and organizations) among a small, more-or-less trusted group of businesses.
Three network challenges
When talking about electronic networks that transfer the ownership of assets between parties, Elli highlighted the accociated issues:
- inefficiency
- expense
- vulnerability
Taking into account the possible impact of these factors on any enterprise, Elli outlined how blockchain addresses the existing network challenges:
- Simplicity. No centralized control points; spreading risks that results in lowered costs; hardened inside vs. perimeter.
- Shared replicated ledger. A peer-to-peer append-only transaction database, replicated across organizational boundaries / legal entities.
- Embedded cryptolayer. Supporting secure authenticated verifiable multi-party transactions via tokenization, digital identity, and digital signatures.
- Business rules evolving to smart contracts. An ability to specify business logic, embed it in the transaction database, and couple execution of the logic with transaction processing.
On the way to transactional privacy
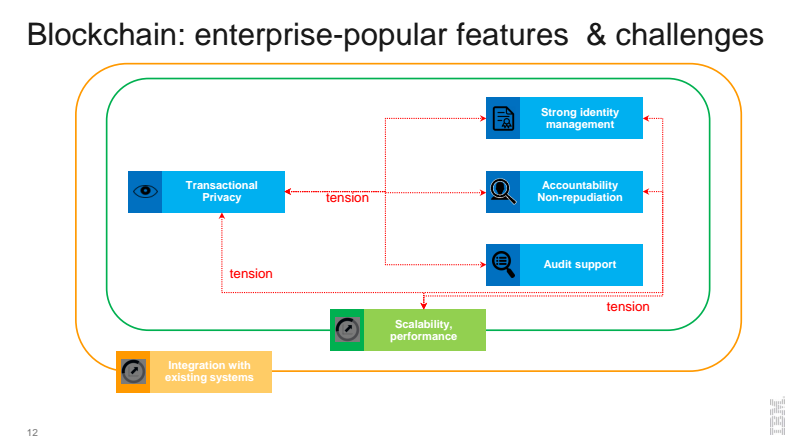
Specifying enterprise needs and the underlying challenges when establishing blockchain, Elli described a series of “tensions” involved. The first level of tensions implies providing transactional privacy, while also guaranteeing strong identity management, non-repudiation (the ability to thwart any attempts at reversing transactions), and audit support. Add to this the complexity of providing the scalability and performance one might expect of a multi-enterprise-grade solution and integrating that into bevies of legacy systems, and the challenge becomes clear.
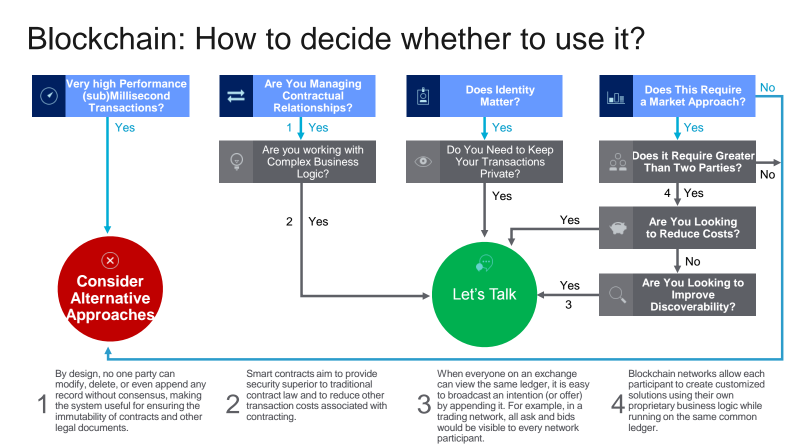
In addition, Elli provided a cheat chart that can be used to to assist people and organizations in making a decision whether blockchain is a match.
The Hyperledger Fabric model
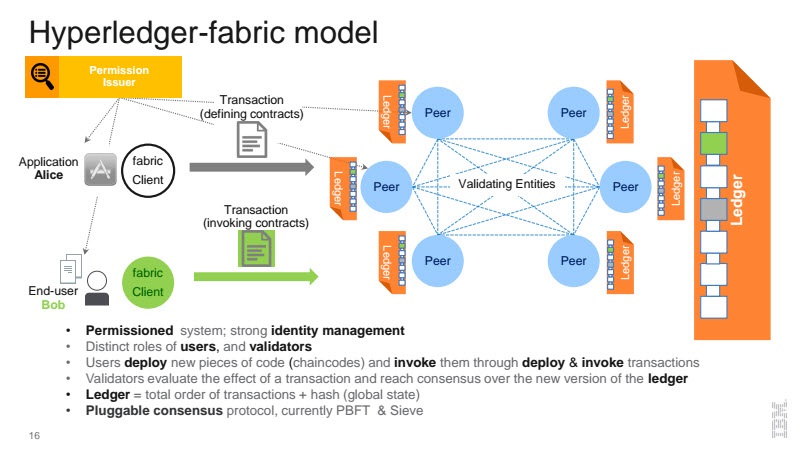
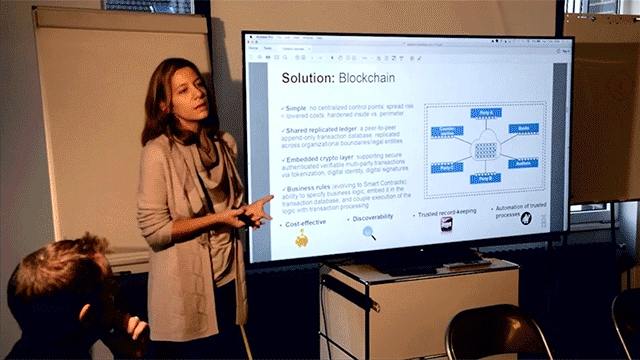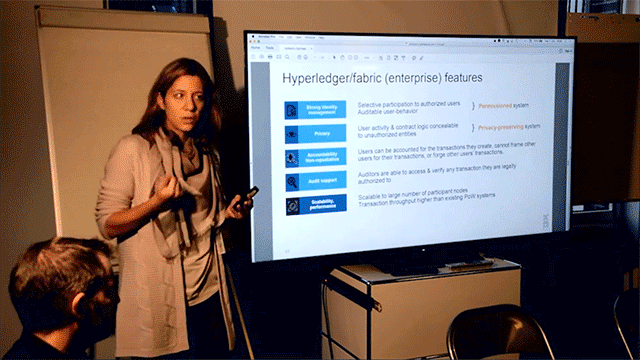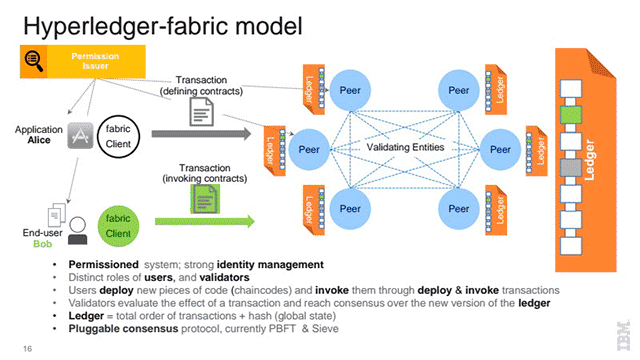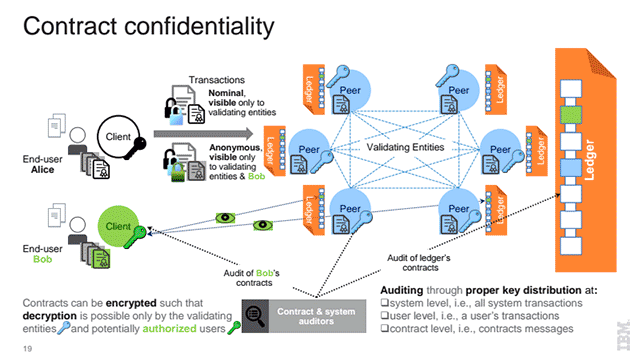
Treating possible ways to defuse these “tensions”, Elli overviewed how Hyperledger Fabric—an open-source blockchain implementation in the Hyperledger project—may help through its key features, membership and contract confidentiality mechanisms, etc.
As the graphic shows, the Fabric is a permissioned system (in which all the players know each other as opposed to the anonymous world of Bitcoin), with strong identity management. In a permissioned system, there are thus distinct roles for the users and the validators. Users invoke and deploy their transactions, which are then validated to create a new version of the blockchain (i.e., ledger). The key cryptographic element is an enhanced version of Practical Byzantine Fault Tolerance (PBFT) known as Sieve.
Trust above all else
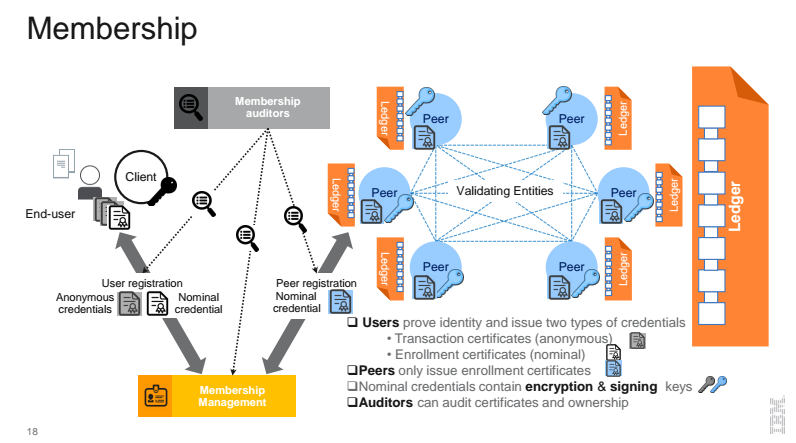
The ultimate measure of Hyperledger projects and all blockchain technology is whether the architecture and implementation can be trusted to validate and secure transactions. With Hyperledger Fabric, the trust starts with selecting and identifying users (who can also be thought of as members in a permissioned system).
In this case, users can prove their identity and issue two types of credentials through either transaction certificates or enrollment certificates, with the latter issued only by peers within this sort of permissioned system. Nominal credentials contain encryption and signing keys, and the designated auditors can audit certificates and ownership.
The underlying trust in this system involves peer institutions each wanting the same clean system that disintermediates those pesky third parties while maintaining the inviolability of transactions and the system in general. A graphic of how membership works follows:
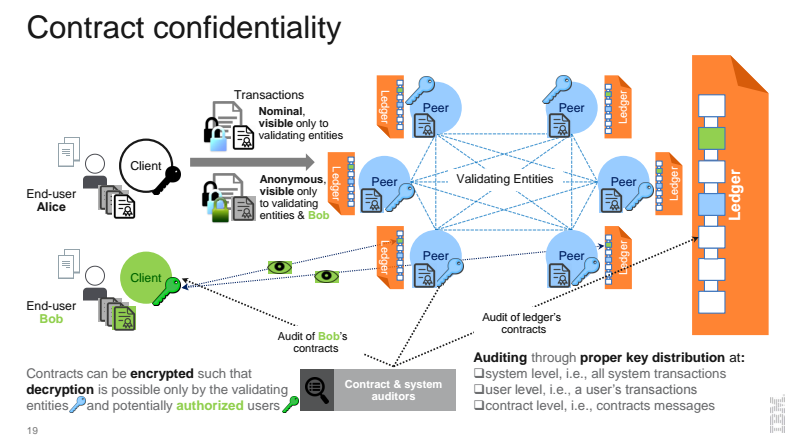
Elli noted that Hyperledger Fabric security is further taken seriously with the use of PBFT and Sieve, enhanced she said by strong identity management and privacy features. She provided an overview graphic of how Hyperledger contracts maintain confidentiality.
What’s next for Hyperlegder Fabric?
The current Fabric implementation is v0.6. Elli concluded her session with revealing the major upcoming features of the v1.0 release:
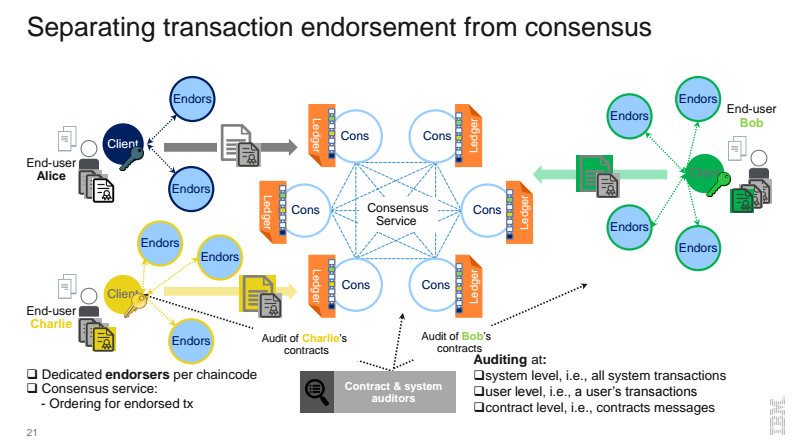
- Separate the functions of validation into endorsers and consensus nodes
- Every chaincode may have different endorsers
- Endorsers have state, run tx, and validate tx for their chaincode
- Consensus nodes order already-validated tx
- Scales better, computation effort can be distributed
- Permits confidential state on blockchain (seen only by endorsers)
Read our next post to learn more about what’s expected in Hyperledger Fabric v1.0 and when.
Want details? Watch the video!
Table of contents
|
Related slides
Related reading
- Hyperledger/Ethereum Discussion Makes P2P/B2B Distinction
- Technical Introduction to Hyperledger Fabric
- Hyperledger Meets Ethereum: Integration and the Future
- Hyperledger/Blockchain Main Drivers, Use Cases, and Implications
About the speaker
with assistance from Carlo Gutierrez and Alex Khizhniak.